Pinpoint the Right Owner for Every Risk
Send security findings directly and automatically to the right teams for prompt resolution.




STREAMLINED RISK WORKFLOW
From noise to simplified resolution with automated mitigation workflows and integration into your security stack.
Send security findings directly and automatically to the right teams for prompt resolution.
Prevent security exploits to ensure effective remediation.
Automate and streamline action items and processes to reduce MTTR and boost efficiency.
With Active Protection, IONIX automatically safeguards the most vulnerable assets from abuse. Dangling DNS records or cloud storage objects (e.g., AWS S3 buckets or Azure blobs) are often vulnerable to attacker hijacking. They can expose web assets to malicious content or DNS takeover. In cases where IONIX detects such vulnerabilities, Active Protection automatically neutralizes the threat – with no action required on your part.
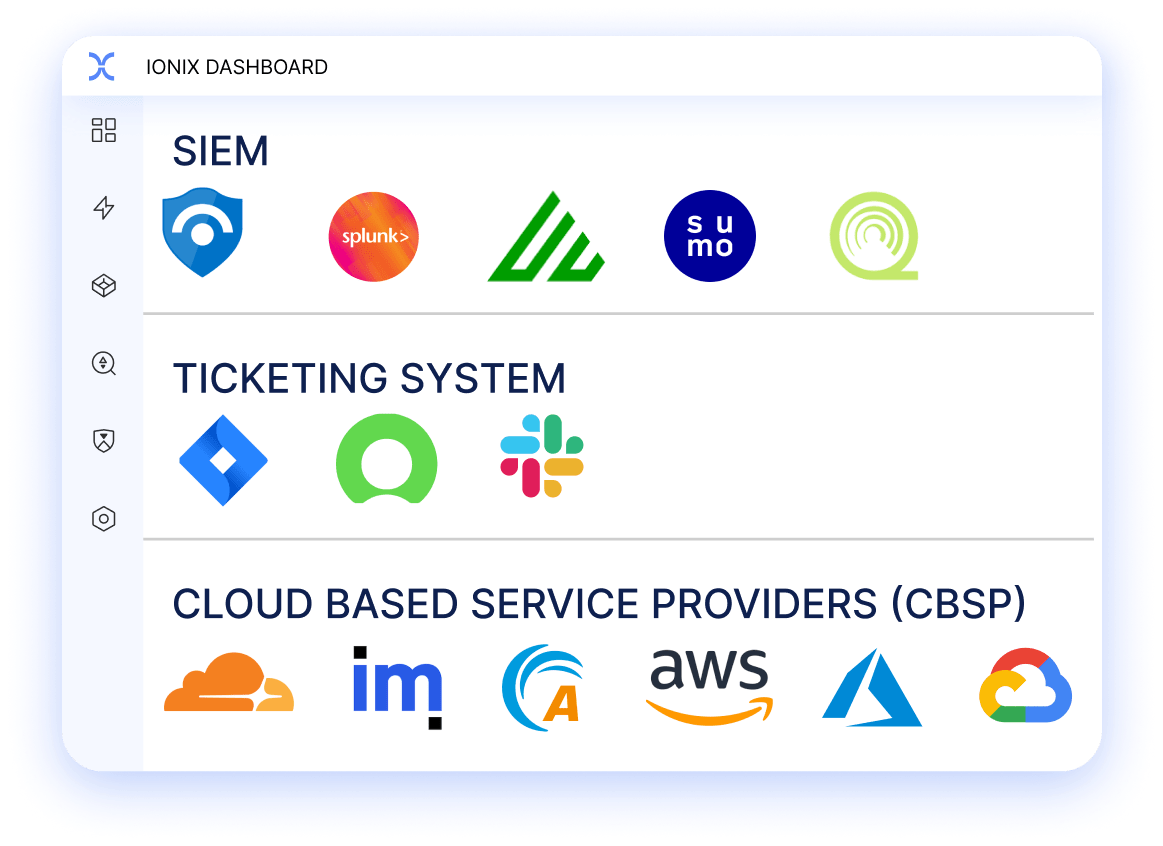
IONIX’s intelligent workflows seamlessly integrate with the natural flow of security operations like system information and event management (SIEM) systems, SOAR, security operations center (SOC) software, and ticketing systems, automating routine tasks and reducing time spent on ticket routing, allowing teams to focus on resolving critical risks and reduce MTTR.
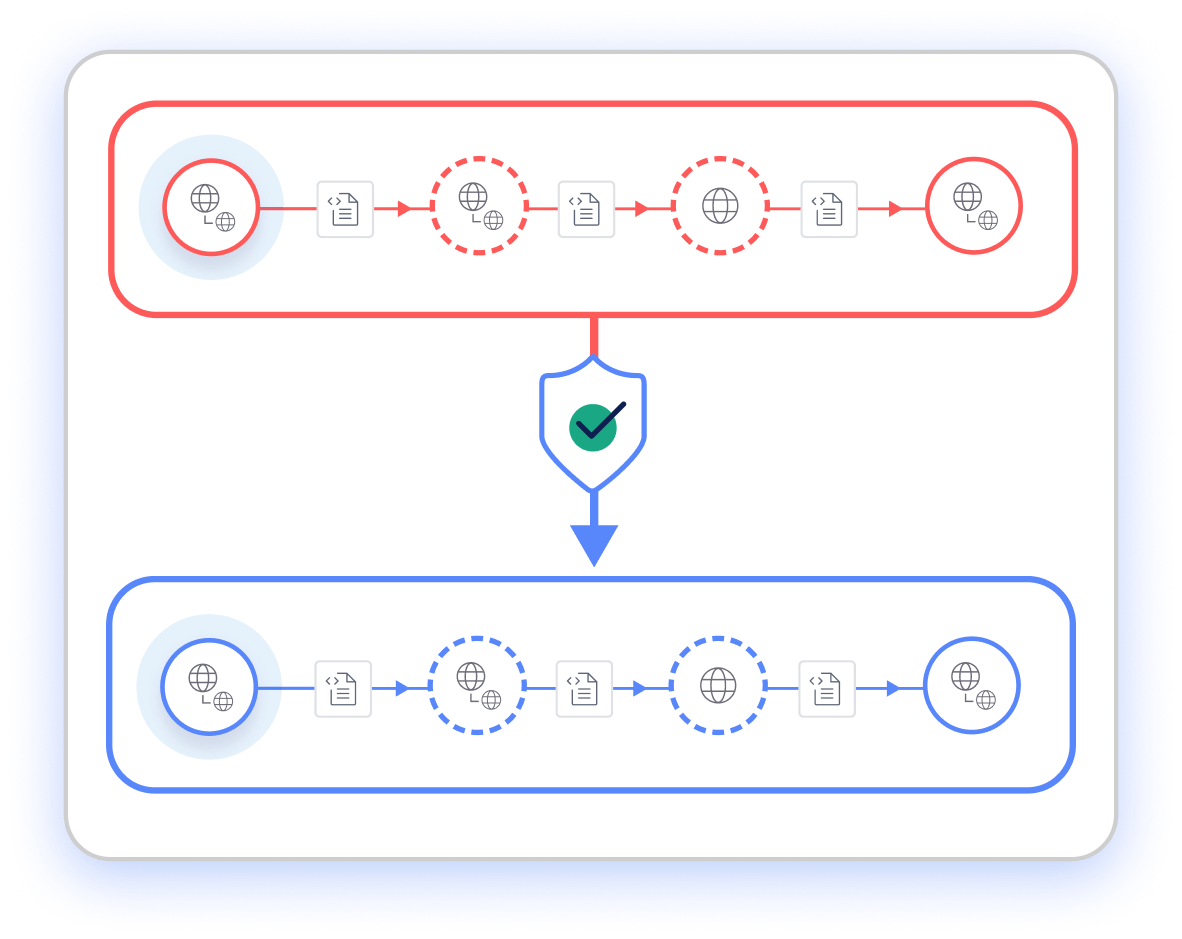
IONIX validates remediation by verifying the effectiveness of applied fixes. It ensures issues were resolved through updated threat intelligence and post-remediation scans, guaranteeing that issues are properly addressed.
In addition, the platform automatically attributes each asset to the relevant subsidiary or business owner – across on-premises, cloud infrastructure, managed services, and 3rd party vendors’ infrastructure.
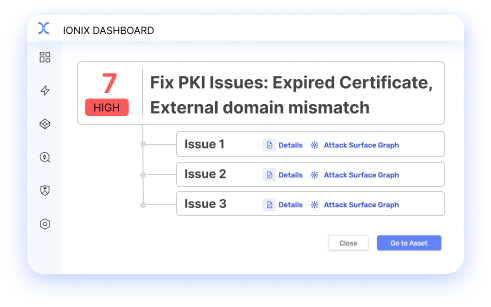
IONIX transforms findings into Action Items. Multiple findings can be grouped into a single Action Item managed by the same team, streamlining efforts and consolidating remediation. This approach increases efficiency and accelerates risk reduction.
Gain clear visibility into your zero-day attack surface exposures to effectively streamline remediation with the IONIX Threat Center. Validate exploitable risks posed by the latest zero-day vulnerabilities that are exploited in the wild.
