CIS Control 1 Explained: Inventory and Control of Enterprise Assets
CIS Control 1 involves keeping a complete and up-to-date current inventory of all devices connected to an organization’s network. This includes personal computers, mobile devices, network hardware, IoT devices and servers. These devices may be physically connected, accessed remotely or located in cloud environments. The objective is to accurately identify and protect every asset within the enterprise.
In this article
The Importance of Control 1
Organizations cannot protect assets they are unaware of. By maintaining a record of all connected devices, security teams gain visibility into both physical and virtual systems. This enables them to monitor, respond to incidents, perform system backups and recover data.
A managed inventory allows for the identification of potential vulnerabilities and the implementation of proactive security measures. Regular monitoring helps detect unauthorized devices accessing the network and addresses them promptly. Additionally, comprehensive asset management enhances incident response by facilitating the quick identification of compromised systems.
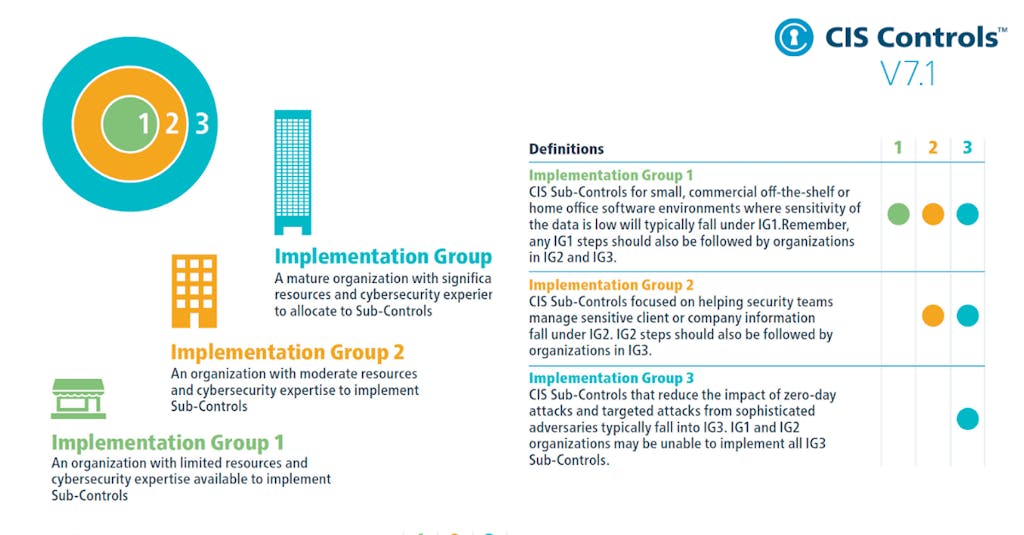
Implementation Groups (IGs)
To implement CIS Controls, follow each listed safeguard, which details the required activities. Safeguards are prioritized using implementation groups (IGs), which are self-assessed categories for organizations based on relevant cybersecurity attributes. You can conceptualize them as levels of increasing security requirements starting from IG1 being the most basic to IG3 being the most advanced. The higher level groups are included in the lower ones.
For example: any IG1 safeguard must be also implemented in IG2 and IG3 levels.
The Safeguards of Control 1
There are five safeguards in CIS Control 1. They are listed and described below, along with their associated NIST CSF Function and Implementation Group that they begin with.
| Safeguard Number | Safeguard Title | NIST Security Function | Starting Implementation Group |
| Safeguard 1.1 | Establish and Maintain Detailed Enterprise Asset Inventory | Identify | IG1 |
| Safeguard 1.2 | Address Unauthorized Assets | Respond | IG1 |
| Safeguard 1.3 | Utilize an Active Discovery Tool | Detect | IG2 |
| Safeguard 1.4 | Use Dynamic Host Configuration Protocol (DHCP) Logging to Update Enterprise Asset Inventory | Identify | IG2 |
| Safeguard 1.5 | Use a Passive Asset Discovery Tool | Detect | IG3 |


