CIS Control 3 Explained: Data Protection
CIS Control 3 involves data protection. This means to develop processes and technical Controls to identify, classify, securely handle, retain and dispose of data.
In this article
The Importance of Control 3
Data now exists outside of an enterprise’s boundaries in context such as the cloud, remote devices and shared with global partners. Sensitive information such as financial, intellectual and customer data must be protected. Enterprises must also adhere to international privacy regulations. Data privacy involves encryption and lifecycle management.
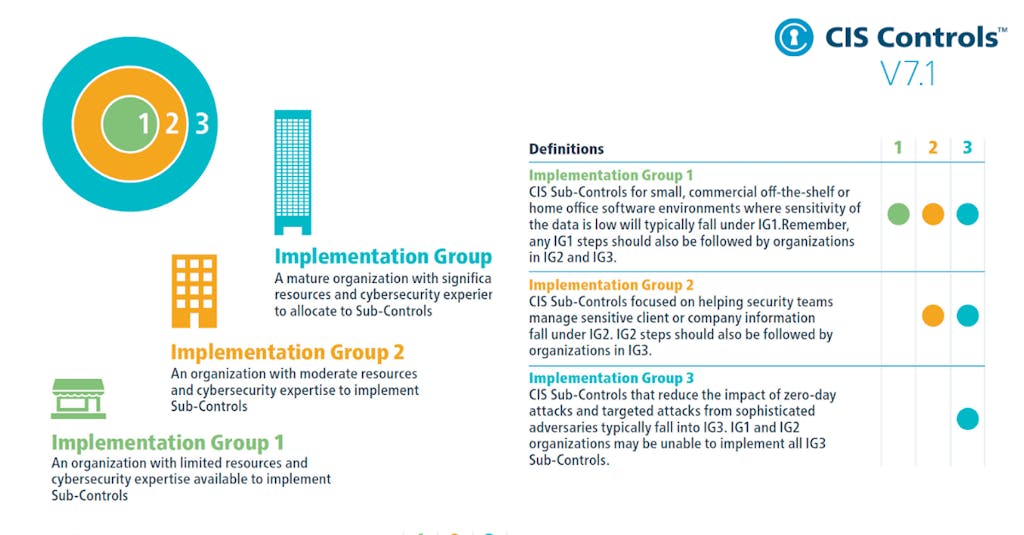
Implementation Groups (IGs)
To implement CIS Controls, follow each listed safeguard, which details the required activities. Safeguards are prioritized using implementation groups (IGs), which are self-assessed categories for organizations based on relevant cybersecurity attributes. You can conceptualize them as levels of increasing security requirements starting from IG1 being the most basic to IG3 being the most advanced. The higher level groups are included in the lower ones.
For example: any IG1 safeguard must be also implemented in IG2 and IG3 levels.
The Safeguards of Control 3
There are fourteen safeguards in CIS Control 3. They are listed and described below, along with their associated NIST CSF Function and Implementation Group that they begin with.
| Safeguard Number | Safeguard Title | NIST Security Function | Starting Implementation Group |
| Safeguard 3.1 | Establish and Maintain a Data Management Process | Govern | IG1 |
| Safeguard 3.2 | Establish and Maintain a Data Inventory | Identify | IG1 |
| Safeguard 3.3 | Configure Data Access Control Lists | Protect | IG1 |
| Safeguard 3.4 | Enforce Data Retention | Protect | IG1 |
| Safeguard 3.5 | Securely Dispose of Data | Protect | IG1 |
| Safeguard 3.6 | Encrypt Data on End-User Devices | Protect | IG1 |
| Safeguard 3.7 | Establish and Maintain a Data Classification Scheme | Identify | IG2 |
| Safeguard 3.8 | Document Data Flows | Identify | IG2 |
| Safeguard 3.9 | Encrypt Data on Removable Media | Protect | IG2 |
| Safeguard 3.10 | Encrypt Sensitive Data in Transit | Protect | IG2 |
| Safeguard 3.11 | Encrypt Sensitive Data at Rest | Protect | IG2 |
| Safeguard 3.12 | Segment Data Processing and Storage Based on Sensitivity | Protect | IG2 |
| Safeguard 3.13 | Deploy a Data Loss Prevention Solution | Protect | IG3 |
| Safeguard 3.14 | Log Sensitive Data Access | Detect | IG3 |


