CIS Control 4 Explained: Secure Configuration of Enterprise Assets and Software
CIS Control 4 involves the secure configuration of enterprise assets and software. This means establishing a continuous process to manage and ensure that all enterprise assets including endpoints, mobile devices, servers, cloud resources and software are configured securely.
In this article
The Importance of Control 4
Not all software and hardware assets are secure in their default configurations. Common issues include default passwords, weak access control policies and unnecessary debugging interfaces, which can create vulnerabilities across various products. Additionally, enterprises often have unique business requirements that necessitate configuration changes such as enabling legacy protocols or using weak cryptography. This further increases their exposure to potential attacks.
Effectively managing security configurations is crucial. Organizations should apply secure default settings for all assets and ensure that any configuration changes or updates go through a formal review and approval process. This helps prevent unauthorized modifications that could compromise security.
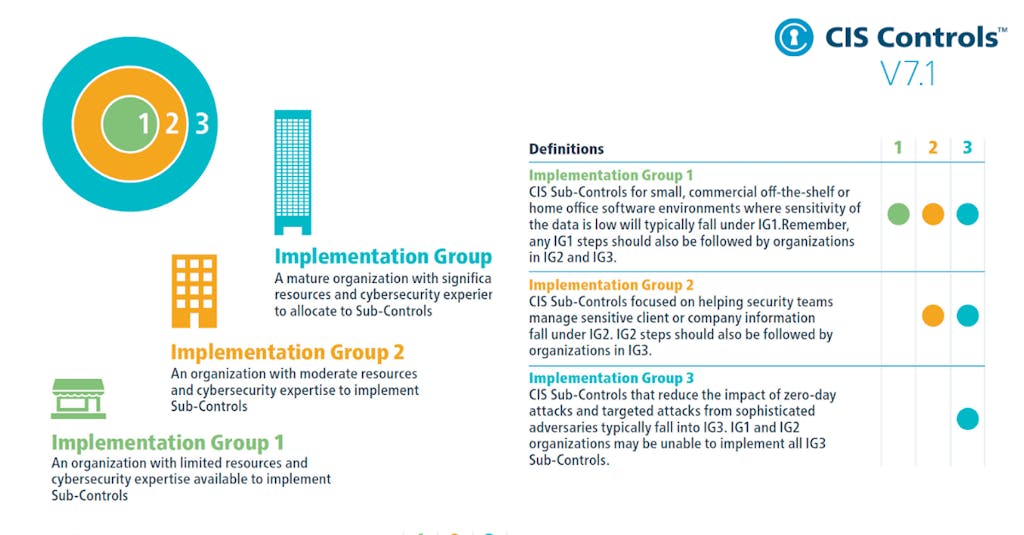
Implementation Groups (IGs)
To implement CIS Controls, follow each listed safeguard, which details the required activities. Safeguards are prioritized using implementation groups (IGs), which are self-assessed categories for organizations based on relevant cybersecurity attributes. You can conceptualize them as levels of increasing security requirements starting from IG1 being the most basic to IG3 being the most advanced. The higher level groups are included in the lower ones.
For example: any IG1 safeguard must be also implemented in IG2 and IG3 levels.
The Safeguards of Control 4
There are twelve safeguards in CIS Control 4. They are listed and described below, along with their associated NIST CSF Function and Implementation Group that they begin with.
| Safeguard Number | Safeguard Title | NIST Security Function | StartingImplementation Group |
| Safeguard 4.1 | Establish and Maintain a Secure Configuration Process | Govern | IG1 |
| Safeguard 4.2 | Establish and Maintain a Secure Configuration Process for Network Infrastructure | Govern | IG1 |
| Safeguard 4.3 | Configure Automatic Session Locking on Enterprise Assets | Protect | IG1 |
| Safeguard 4.4 | Implement and Manage a Firewall on Servers | Protect | IG1 |
| Safeguard 4.5 | Implement and Manage a Firewall on End-User Devices | Protect | IG1 |
| Safeguard 4.6 | Securely Manage Enterprise Assets and Software | Protect | IG1 |
| Safeguard 4.7 | Manage Default Accounts on Enterprise Assets and Software | Protect | IG1 |
| Safeguard 4.8 | Uninstall or Disable Unnecessary Services on Enterprise Assets and Software | Protect | IG2 |
| Safeguard 4.9 | Configure Trusted DNS Servers on Enterprise Assets | Protect | IG2 |
| Safeguard 4.10 | Enforce Automatic Device Lockout on Portable End-User Devices | Protect | IG2 |
| Safeguard 4.11 | Enforce Remote Wipe Capability on Portable End-User Devices | Protect | IG2 |
| Safeguard 4.12 | Separate Enterprise Workspaces on Mobile End-User Devices | Protect | IG3 |


