CIS Control 6 Explained: Access Control Management
CIS Control 6 involves access control management. This means using tools and processes to assign, manage and revoke access credentials and privileges for accounts on all enterprise and software assets.
In this article
The Importance of Control 6
Effective access control management helps mitigate the risks of insider threats, where authorized users misuse their privileges for malicious purposes and reduces the potential for lateral movement by attackers who have gained access to compromised systems and accounts within your organization. This applies to user, administrator and service accounts. While some may present greater risks than others, those risks remain unclear without proper account management processes that provide visibility into the data they can access and the actions they can perform.
This control also encompasses authentication security measures, such as multi-factor authentication (MFA) and single sign-on (SSO), to ensure centralized access control. These measures are particularly crucial for external-facing and administrative applications, as they prevent attackers from logging in with stolen credentials and accessing sensitive systems.
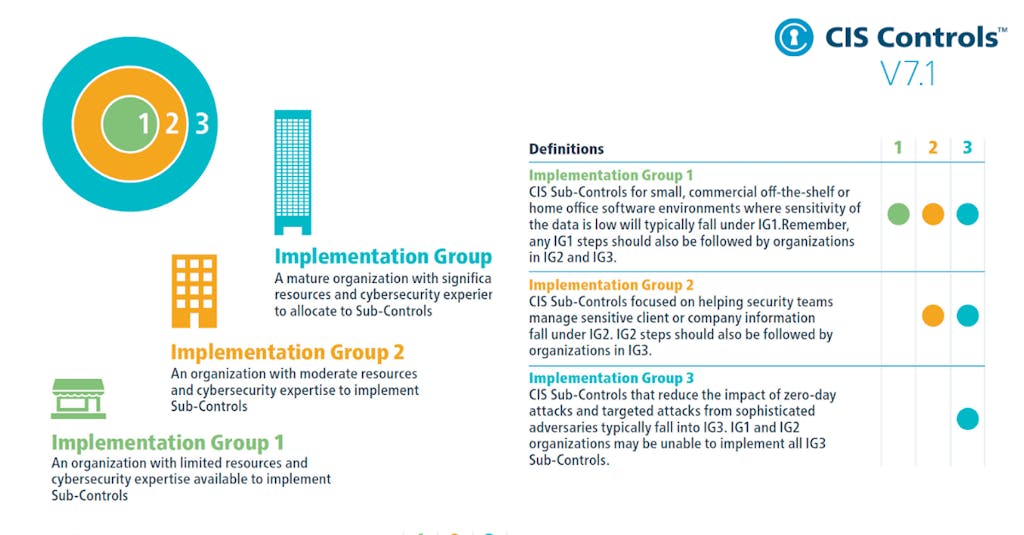
Implementation Groups (IGs)
To implement CIS Controls, follow each listed safeguard, which details the required activities. Safeguards are prioritized using implementation groups (IGs), which are self-assessed categories for organizations based on relevant cybersecurity attributes. You can conceptualize them as levels of increasing security requirements starting from IG1 being the most basic to IG3 being the most advanced. The higher level groups are included in the lower ones.
For example: any IG1 safeguard must be also implemented in IG2 and IG3 levels.
The Safeguards of Control 6
There are eight safeguards in CIS Control 6. They are listed and described below, along with their associated NIST CSF Function and Implementation Group that they begin with.
| Safeguard Number | Safeguard Title | NIST Security Function | StartingImplementation Group |
| Safeguard 6.1 | Establish an Access Granting Process | Govern | IG1 |
| Safeguard 6.2 | Establish an Access Revoking Process | Govern | IG1 |
| Safeguard 6.3 | Require MFA for Externally-Exposed Applications | Protect | IG1 |
| Safeguard 6.4 | Require MFA for Remote Network Access | Protect | IG1 |
| Safeguard 6.5 | Require MFA for Administrative Access | Protect | IG1 |
| Safeguard 6.6 | Establish and Maintain an Inventory of Authentication and Authorization Systems | Identify | IG2 |
| Safeguard 6.7 | Centralize Access Control | Protect | IG2 |
| Safeguard 6.8 | Define and Maintain Role-Based Access Control | Govern | IG3 |


