CIS Control 16 Explained: Application Software Security
CIS Control 16 involves application software security. That means to manage security of in house developed/hosted/acquired software, by establishing a software security lifecycle to prevent, detect and remediate software security weaknesses.
In this article
The Importance of Control 16
Application vulnerabilities can arise from various factors, including insecure design, inadequate infrastructure, coding errors, weak authentication and insufficient testing for unexpected conditions. Attackers can exploit these vulnerabilities – such as Structured Query Language injection (SQLi), Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF) to access sensitive data or take control of vulnerable assets, which can serve as a launching point for further attacks.
Implementation Groups (IGs)
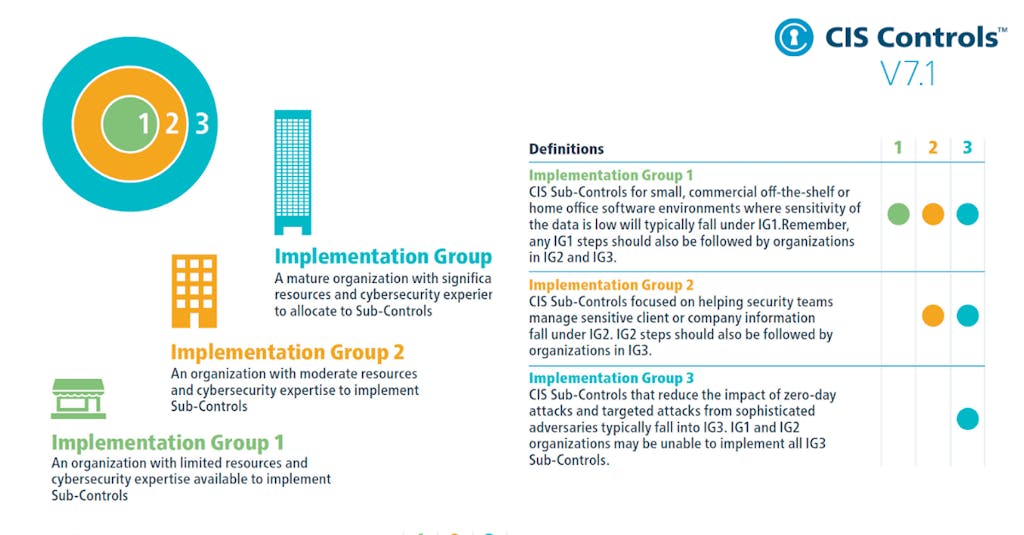
To implement CIS Controls, follow each listed safeguard, which details the required activities. Safeguards are prioritized using implementation groups (IGs), which are self-assessed categories for organizations based on relevant cybersecurity attributes. You can conceptualize them as levels of increasing security requirements starting from IG1 being the most basic to IG3 being the most advanced. The higher level groups are included in the lower ones.
The Safeguards of Control 16
There are fourteen safeguards in CIS Control 16. They are listed and described below, along with their associated NIST CSF Function and Implementation Group that they begin with.
| Safeguard Number | Safeguard Title | NIST Security Function | StartingImplementation Group |
| Safeguard 16.1 | Establish and Maintain a Secure Application Development Process | Govern | IG2 |
| Safeguard 16.2 | Establish and Maintain a Process to Accept and Address Software Vulnerabilities | Govern | IG2 |
| Safeguard 16.3 | Perform Root Cause Analysis on Security Vulnerabilities | Protect | IG2 |
| Safeguard 16.4 | Establish and Manage an Inventory of Third-Party Software Components | Identify | IG2 |
| Safeguard 16.5 | Use Up-to-Date and Trusted Third-Party Software Components | Protect | IG2 |
| Safeguard 16.6 | Establish and Maintain a Severity Rating System and Process for Application Vulnerabilities | Govern | IG2 |
| Safeguard 16.7 | Use Standard Hardening Configuration Templates for Application Infrastructure | Protect | IG2 |
| Safeguard 16.8 | Separate Production and Non-Production Systems | Protect | IG2 |
| Safeguard 16.9 | Train Developers in Application Security Concepts and Secure Coding | Protect | IG2 |
| Safeguard 16.10 | Apply Secure Design Principles in Application Architectures | Protect | IG2 |
| Safeguard 16.11 | Leverage Vetted Modules or Services for Application Security Components | Identify | IG2 |
| Safeguard 16.12 | Implement Code-Level Security Checks | Protect | IG3 |
| Safeguard 16.13 | Conduct Application Penetration Testing | Detect | IG3 |
| Safeguard 16.14 | Conduct Threat Modeling | Protect | IG3 |


