Outside-in Cloud Security
See vulnerabilities through an attacker’s eyes to expose real threats




See vulnerabilities through an attacker’s eyes to expose real threats
Prioritize cloud security findings using non-intrusive exploit validation
Attack paths across public, private, and multi-cloud deployments
IONIX empowers security teams to prioritize vulnerabilities with an attacker-centric view, filtering out theoretical risks and spotlighting real, exploitable threats. By identifying and addressing the critical risks attackers are most likely to target, IONIX enables immediate, targeted action.

IONIX’s Cloud Cross-View enhances visibility into your cloud environments by enriching ASM data with internal cloud data. This combination offers a comprehensive view of your complete attack surface, enabling you to manage cloud assets risks not only based on vulnerabilities but also on level of exposure.

IONIX Cloud Exposure Validator integrates with CSPM platforms like Wiz and Prisma Cloud to refine security findings with IONIX’s unique external exposure insights. It examines exploitability and asset context, determining if weaknesses are accessible from outside. The Validator analyzes and re-prioritizes alerts from cloud security tools based on actual exploitation and severity, enabling organizations to allocate resources to address the most critical issues first.
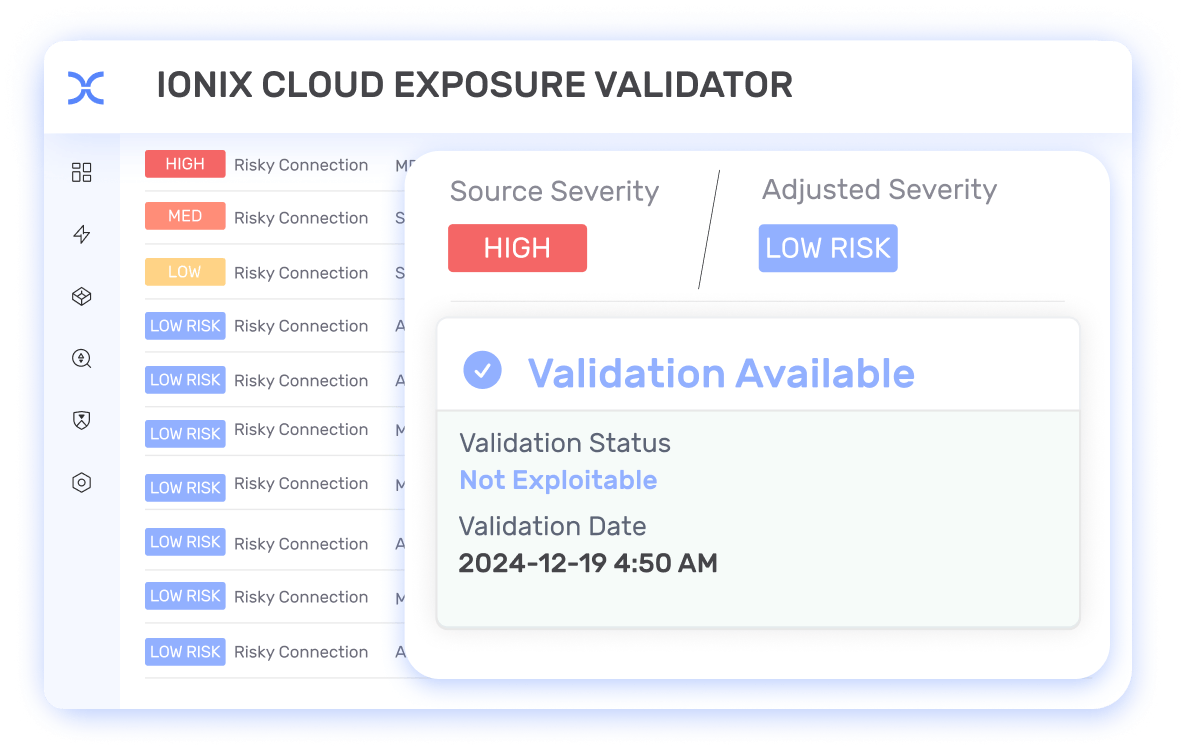
IONIX Connective Intelligence maps and analyzes critical dependencies between assets across multiple clouds and hybrid environments, revealing how seemingly isolated vulnerabilities can form dangerous attack chains. By visualizing these relationships in dynamic Attack Path Graphs, IONIX enables security teams to proactively identify, assess, and prioritize threats across their entire attack surface based on real-world exploit potential rather than isolated vulnerability scores.
See how easy it is to implement a CTEM program with IONIX. Find and fix exploits fast.