OWASP Top 10: Software and Data Integrity Failures
Companies commonly use third-party applications or include external libraries and dependencies within their applications. This means that they trust this code to be correct both now and in the future.
In this article
With software updates, applications may accept and execute code from a third-party source under the assumption that it is authentic and benign. These practices — classified as Software and Data Integrity Failures by the OWASP Top Ten — expose these systems to various threats.
What is the Risk?
If an application uses third-party libraries, it will likely need to update these libraries at some point. This involves adding new code to the organization’s codebase and executing it.
If a development team doesn’t properly validate the update code, it’s possible that an attacker may have sent out a malicious update or corrupted a legitimate one. If this is the case, any application using this code has been infected with malware, which could steal sensitive data, perform a Denial of Service (DoS) attack, or execute other malicious actions.
Examples of Attack Scenarios
Developers commonly use third-party code and data in their applications. If this external content is trusted and not adequately validated, an attacker can take advantage of this error in various ways, including the following:
Third-Party Libraries
Most applications use some amount of third-party code. Importing libraries and packages is faster and easier than writing the same code from scratch. Additionally, the careful use of external code can improve code quality, security, and capabilities.
However, the source of these dependencies has a significant impact on code security. Supply chain attacks commonly target popular open-source projects, attempting to inject malicious code into a widely used library. Attackers may also create lookalike projects or work to compromise existing accounts to distribute malware.
If an application imports a malicious dependency, the attacker’s code may be run by that software. This provides the attacker with the same privileges as the vulnerable application and can be used to steal sensitive data, deploy additional malware, or take other malicious actions on the system.
AI-Generated Code
With the rise of LLM chatbots like ChatGPT and AI coding assistants, code developed by AI has been creeping into production applications. This may be through code copy-pasted from a chat window or software autonomously generated by a coding assistant.
This is problematic because AI-generated code is prone to errors. It’s derived from code scraped from the Internet, which can contain various errors. In the past, GenAI tools have been known to recommend the use of non-existent third-party libraries.
This provides an opening for an attacker to create these recommended libraries and incorporate malicious code. If AI-generated code works and recommends a particular library, developers may not notice that their imported code is actually malware.
Serialized Data
This OWASP vulnerability class addresses failures related to both code and data security. On the data side, one of the biggest threats is serialized data.
Serialized data converts objects and structures into a string that can be easily transmitted and unpacked at its destination. Often, the recipient trusts the data to follow a particular format and unpacks it accordingly into a set of variables.
This creates an opportunity for an attacker who can cause trusted, serialized data to violate this assumption. If the data has been modified in a way that defies expectations, this may allow the attacker to control variables that they shouldn’t be able to access. This type of vulnerability can be used in various ways, such as privilege escalation or to achieve remote code execution (RCE).
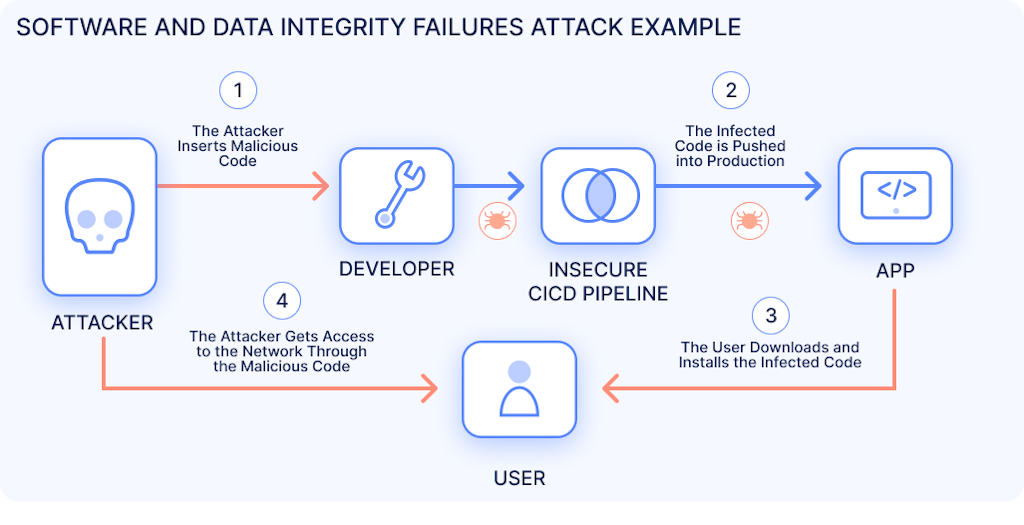
Case Study: SolarWinds
The 2020 SolarWinds breach is likely the most famous example of this type of vulnerability. Attackers who managed to gain access to the company’s development environment inserted malicious code into an update to the SolarWinds Orion network monitoring solution. Since this was a legitimate update, the malicious code was digitally signed by the company and pushed out to its customers.
Once the update was installed, the attacker had backdoor access to the networks of an estimated 18,000 customers. Since the Orion user list included Fortune 500 companies and government agencies, they had the opportunity to steal highly sensitive data or take other actions to further compromise these environments.
How to Remediate Software and Data Integrity Failures
Best practices to protect against vulnerabilities caused by failures in software and data integrity include the following:
- Validate Code Integrity: Third-party code may have been created or modified by an attacker to contain vulnerabilities or malicious functionality. Use digital signatures or file hashes to verify code integrity and authenticity before use.
- Use Trusted Repositories: Applications can source third-party dependencies from various repositories. Restricting sources of third-party code to known, trusted repositories lowers the risk of importing malicious or vulnerable code.
- Manage Supply Chain Vulnerabilities: Third-party libraries and packages may contain exploitable vulnerabilities. Tracking these dependencies and monitoring for new vulnerabilities is essential to managing the associated risk.
- Verify Serialized Data: Serialized data can be modified to exploit vulnerable recipients. Ensure that all data being sent to untrusted clients is digitally signed or encrypted to ensure integrity.
How IONIX Can Help
The OWASP Top Ten list details the most common and significant vulnerabilities in web applications. Software and data integrity failures was a new category in the 2021 update to the list and was designed to address potential supply chain vulnerabilities in applications.
As cybercriminals increasingly use supply chain attacks to scale their campaigns and maximize impact, visibility into these vulnerabilities is critical for security. The IONIX platform helps organizations identify these and other OWASP vulnerabilities via simulated attacks during a proactive risk assessment. To learn more about managing your digital attack surface with IONIX, request a free demo.



