More Assets Less Noise
IONIX crawls web-facing assets and analyzes based on 13 components to determine asset ownership without a doubt.




IONIX crawls web-facing assets and analyzes based on 13 components to determine asset ownership without a doubt.
The only ASM provider to look at assets deep into the digital supply chain including 3rd, 4th… party assets connected to your infrastructure.
ML-based asset attribution proves assets belong to you so that attribution properties are completely transparent.
Proprietary “Connective Intelligence” technology maps context and dependencies between assets, including asset importance.
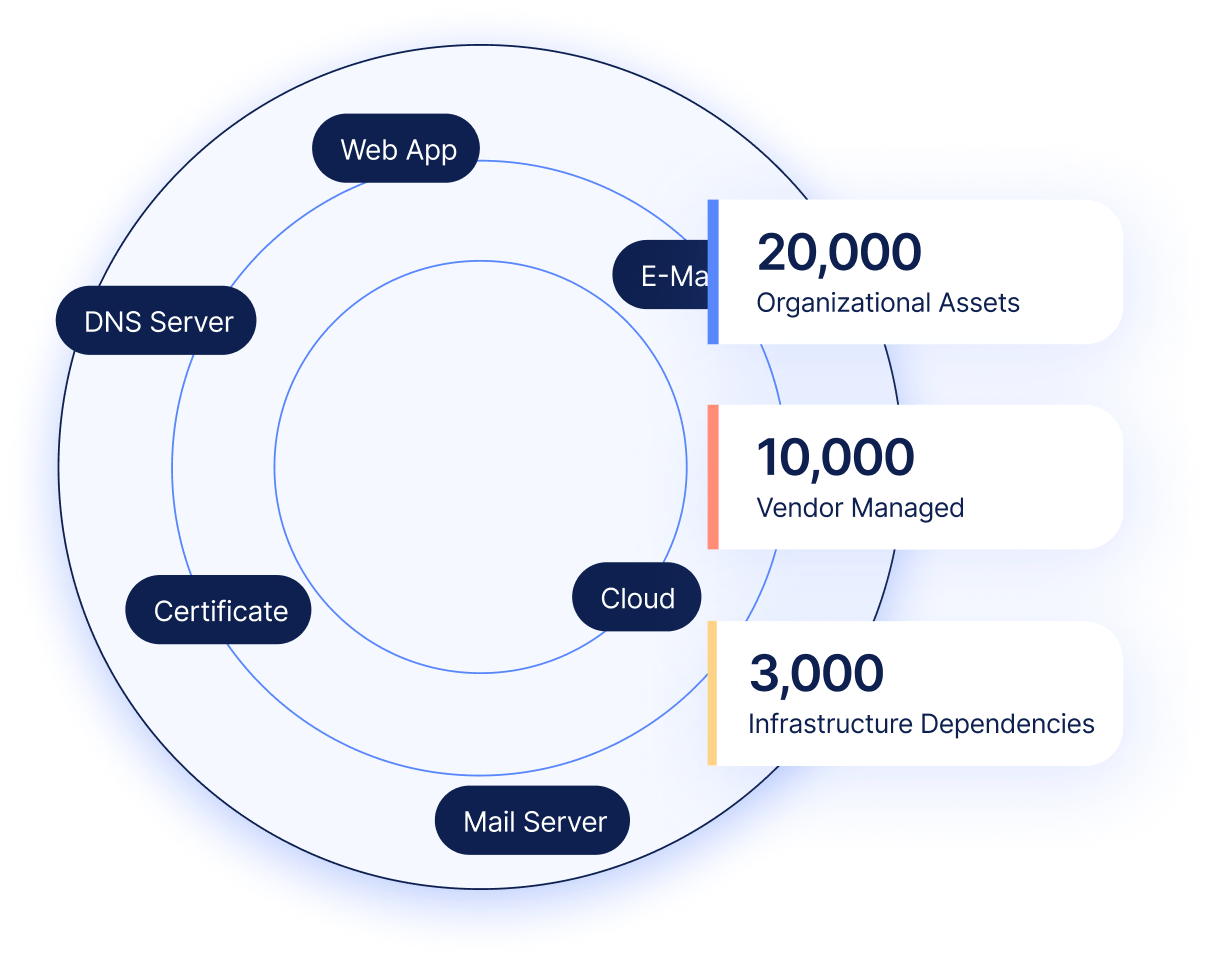
Enhanced by machine learning, IONIX scans your digital footprint using multiple data sources and 13 advanced techniques, uncovering even the most elusive assets across organizational, cloud assets and vendor-managed assets.
In addition, unlike other ASM tools, IONIX adds infrastructure dependencies to the attack surface footprint, offering the widest ASM coverage in the market.
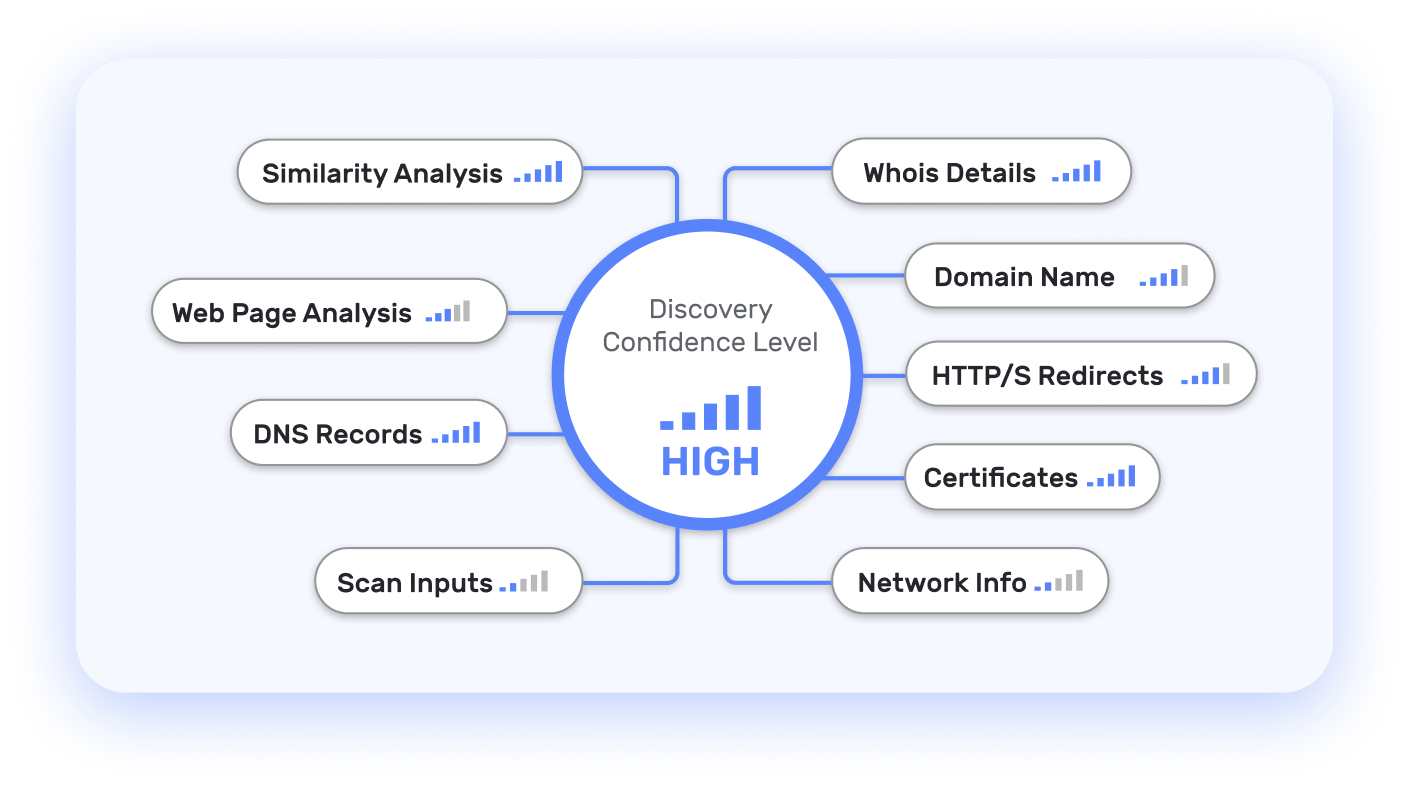
Understand the asset attribution logic with detailed evidence and intuitive visualizations. Gain confidence in the accuracy and relevance of every asset identified within your attack surface by exploring the attribution process.
IONIX’s Cloud Cross-View enhances visibility into your cloud environments by enriching ASM data with internal cloud data and enhancing insights from CSPM tools. This combination offers a comprehensive view of your complete attack surface, enabling you to manage cloud asset risks not only based on vulnerabilities but also on level of exposure.
Securing the digital supply chain is complex due to interconnected IT environments and third-party dependencies. IONIX leverages advanced discovery capabilities to monitor and map these assets, identifying vulnerabilities and prioritizing critical risks. This enables proactive measures to secure your digital supply chain effectively.

IONIX Connective Intelligence identifies risky connections and dependencies between assets to expose how vulnerabilities can create attack chains, enabling proactive assessment and prioritization of potential threats across your entire attack surface. IONIX plots this information on an Attack Path Graph to provide context and highlight prioritized exposures.
