Asset Importance: The Overlooked Cyber Risk Factor

This blog post delves into a critical yet often neglected aspect of cyber risk analysis —adding organizational context by understanding and prioritizing the importance of assets. Without considering the unique business context of an organization, security teams cannot effectively prioritize and remediate what matters most to their organization.
In this article
The Challenge of Cyber Risk Prioritization
In today’s cyber-security landscape, organizations’ attack surfaces are becoming wider and more complex. The challenges of risk prioritization and remediation are becoming increasingly difficult, especially for large organizations, which have thousands of assets and risks.
The Need for Organizational Context in Cyber Risk Analysis
Prioritizing assets for remediation is typically done based on a risk assessment that focuses on the vulnerabilities, misconfigurations, and security issues the asset has. This is often done based on general industry practices and standards, which may not reflect the specific organization’s needs, within its particular business context. As a result, important assets are not always prioritized, and security risks are not mitigated efficiently.
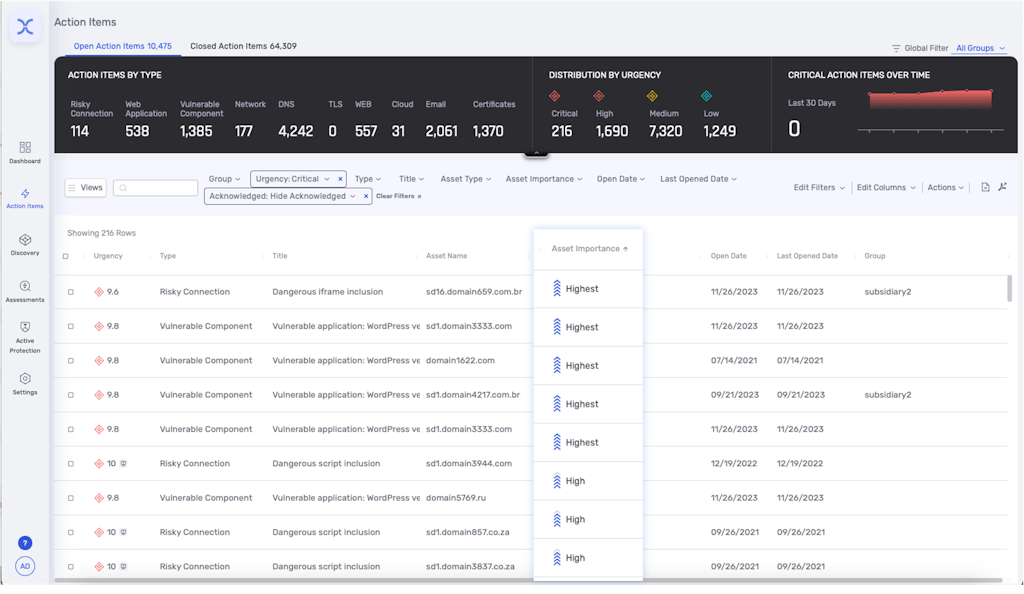
Prioritize Remediation with Importance Ranking
Asset importance ranking aims to solve the problem of organizations struggling to prioritize their vulnerability remediation efforts in the face of a constantly evolving attack surface. By utilizing the right indicators, metrics and calculations that rank every asset, organizations can gain a better understanding of which parts of their business and infrastructure are most critical to their operations and success or even have the potential to damage operations and have a negative impact on financial outcomes.
With asset importance ranking, organizations can prioritize based on risk criticality as well as the impact to the organization in case of a breach.
Prioritize What’s Urgent and Important – Key Considerations for Effective Asset Ranking
1. Be organization-focused
Web ranking solutions compare the organization’s domains to the entire web or the most popular sites. The context here is the importance of the assets you own to your organization and not the importance of the assets to the world. Web ranking adds value, but is surely not a single point of indication to rely on.
2. Your organization is unique and evolving
Due to the unique nature of every organization and the behavior of various asset types, static benchmarks can be outdated and irrelevant fairly quickly. In addition, you would need to map out the external facing digital assets and ones that are not accessible via the web.
3. Business context matters
Without analyzing the assets within the organization’s business context, ranking solutions will always be limited. The blast radius of a breach will not always be measured by the technical damage caused but by the financial impact, if in dollars of brand equity.
4. Consider multi-factor analysis
The type of asset or number of visitors isn’t enough to understand the importance of an asset. An accurate, comprehensive understanding of an asset’s importance level can be reached only by performing a multi-factor analysis and comparison of the entire organization’s attack surface. When ranking, we will need to identify and analyze complex factors that are often overlooked, such as usage of web policies, SSL configurations, as well asset connectivity within the organization and to 3rd parties.
5. Aim for total visibility
Before jumping in, you will need to invest in a deeper discovery process. Having a complete and up-to-date attack surface visibility will help fine-tune your data set and ensure that your organization’s importance ranking truly represents your organization’s assets across hybrid IT environments; on-premises, clouds, etc.
Weighted Calculations for Indicating Asset Importance
How are attack surface assets ranked by importance?
Classifying assets into different levels of importance provides significant benefits to organizations in terms of visibility and understanding of their attack surface. This enables them to focus their remediation efforts on the few assets that matter most to the organization. The following list explains some of the key factors in asset ranking:
Asset Sensitivity
This is the likelihood of finding or reaching sensitive data via the asset. This could include factors such as the type and amount of sensitive data the asset holds, the potential impact of a breach on the organization’s customers or partners, or the potential impact on the organization’s regulatory compliance. Sensitive assets can be, for example, internal databases, user management DBs systems that contain credential and secret tokens, or API endpoints connecting to sensitive data.
Business Context
Business context relates to relevance of an asset to the organization’s revenue-generating activities. For example, an ecommerce domain with a high business score will usually have a large number of visitors and traffic, a high financial value, and a significant role in the organization’s operations and business processes. If that asset is shut down – even for a few minutes – revenue would be directly impacted.
Organization Reputation
Reputational factors are things that may cause potential damage to the organization’s reputation, users’ trust and loss of revenue.
Network Dependencies
These are assets that your company domains rely on or those that are essential to the organization’s overall operations. These assets are typically interconnected with other assets in the organization’s network, and play a crucial role in enabling the organization to conduct its business. Network dependencies mainly refer to assets that have many connections, for example DNS and Mail Servers.
Applying Contextual Indicators
The following factors help to determine the context of an asset as it relates to other important assets:
- The number and type of connections going in and out of the asset.
- For example, look at how many scripts and resources are pulled from this asset by other assets. If this asset is compromised it may create a domino effect.
- Another example can be connections going out, if an asset is acting as a ‘centralized junction’, that also can indicate importance.
- Maintenance. The assumption here is that important assets are looked after and highly maintained. For example, assets with valid certificates.
- Domain authority. Analyzing traffic, engagement, and domain authority scores, based on: visits (unique and not unique), traffic rank (global, country, and category ranks), bounce rank, backlinks, domain age, etc.
- Asset type. For example, Test and Dev sites will likely be less important to the ongoing operation of an organization than APIs, VPNs, or externally facing customer login pages.
- DNS and Network configurations. These can give a good indication of importance when ranking. For example if an asset has a MX record it indicates a higher level of importance.
- Domain name analysis.
- Second level domain length for example, google.com, would probably be more important than googlemarketingwebsite.com
- Subdomain names such as 12345test.test.domain.com would be less important than api.domain.com
Taking all the above indicators into account, along with many others, can give a raw score for each asset that can be adjusted using the weighted factors. Once you have that, the collected scores can be spread out and converted to percentiles.
Percentiles are used because the weighting is not absolute. At IONIX, our aim is to prioritize the assets we want to work on first within the existing limitation of resources. My personal recommendation is defining the highest tier to include around 2%-5% of the total number of organizational assets, as this will keep your operation highly focused.
Finally, remember that having an asset importance score needs to be combined with the potential risk and vulnerabilities found on each asset, so it’s an important metric but not the only one that should be looked at when conducting your final prioritization.
Asset Importance Ranking is Critical
Asset importance ranking plays a critical role in cyber risk prioritization; one that is often overlooked. To effectively prioritize risks, traditional risk assessment is not enough. Security teams need to consider the unique business context of the asset at risk. Asset importance ranking requires a nuanced approach that evaluates assets based on asset sensitivity, business impact, and network dependencies, among other factors. By integrating these considerations, organizations can focus their remediation efforts on the most critical assets, ensuring efficient use of resources and enhanced security posture.
Ready to see how asset importance ranking can transform your organization’s security strategy? Get a free scan today to see your rankings.






