How are Attack Vectors Related to Your Attack Surface?
Attack Surface vs. Attack Vectors Explained
In the world of cybersecurity, two terms frequently dominate discussions among professionals: “Attack Surface” and “Attack Vectors”. At first glance, these concepts might appear separate, but they are intricately linked, shaping the way security experts strategize and implement defenses. When considering your organization’s cybersecurity strategy, it’s important to differentiate between ‘Attack vector vs attack surface’—one focuses on the paths an attacker might use, while the other refers to the total number of vulnerable points in your system. Below is an image showcasing some of the topics we will speak on today.

What is an Attack Surface?
An attack surface contains all the possible points where a bad actor can try to enter data to or extract data from an environment. Think of it as the “digital real estate” that your organization exposes to any potential threats. This surface expands across various dimensions, from physical devices like laptops, servers, and phones to digital domains like networks and software applications. Your attack surface even encompasses the human element, such has your employees and their vulnerability to social engineering attacks.
What is an Attack Vector?
On the other side of the coin are attack vectors. There are varying types of attack vectors. These are methods or pathways a bad actor employs to gain access to a computer system, network, database, warehouse, etc. Attack vectors can range from sophisticated malware and phishing scams to exploiting vulnerabilities in web applications or leveraging zero-day exploits. Essentially, they are the tools and tactics used to exploit weaknesses in an organization’s attack surface.
Putting Them Together
Understanding the relationship between these two concepts is crucial in today’s cybersecurity landscape. A broad attack surface can present lots of opportunities for attackers, making it imperative for organizations to not only identify and understand their attack surfaces, but also to anticipate the potential attack vectors that could be used against that attack surface.
In this blog, we’ll delve deeper into what constitutes an attack surface, explore various attack vectors, and examine how these two elements come together to impact an organization’s security posture. Whether you’re a seasoned security professional or a curious learner, this exploration aims to enhance your understanding and provide insights into effectively managing attack surface and handling possible attack vectors.
Understanding Attack Surfaces
The concept of an attack surface is central to any discussion about an organization’s cybersecurity posture. It refers to all the points where an attacker can try to enter or extract data. Anything that a bad actor has access to, is considered a part of an organization’s attack surface. And it is surprising just how much that entails. Understanding your attack surface is the first step in securing your network and data. Here are some common examples of attack surface:
- Physical Attack Surface: This includes all the physical components like servers, computers, phones, and offices. It is anything tangible that can be physically accessed or compromised.
- Digital Attack Surface: This encompasses the software, networks, and technology stack your organization uses. It includes:
- Web applications and websites.
- Network equipment like routers and switches.
- Cloud services, storage solutions, and accounts.
- Software vulnerabilities on unpatched or outdated components.
- Human Attack Surface: Often overlooked, this involves the people in your organization. Employees can be vulnerable to:
- Social engineering attacks like phishing.
- Insider threats, either intentional or accidental.
Identifying and regularly reviewing your attack surface is not a one-time task but a continuous effort. It is about understanding not only where your assets are, but also how they can be potentially exploited.
If you are interested in reading more about attack surfaces and how to protect them, check out this blog in Enterprise Security Online.
Exploring Attack Vectors
An attack vector is a method of pathway used by a bad actor to access a network or system, often exploiting a vulnerability within the system. Here are some examples of common types of attack vectors:
- Phishing: A form of social engineering where attackers trick victims into giving away sensitive information or access.
- Malware: Malicious software, including viruses, worms, trojans, and ransomware, that disrupts or damages a system.
- SQL Injection: An attack that involves injecting malicious language into SQL queries to manipulate databases into doing something that they were not meant to do.
- Zero-Day Exploits: These are attacks targeting vulnerabilities that are not yet known to the software vendor or the public.
- Man-in-the-Middle (MitM) Attacks: The attacker secretly intercepts and possibly alters the communication between two unknowing parties.
- Denial-of-Service (DoS) Attacks: These attacks aim to shut down a network or service, making it inaccessible to its intended users.
- Weak and Stolen Credentials: This involves attackers gaining unauthorized access through compromised or easily guessable usernames and passwords. Weak credentials are often the result of poor password management or phishing attacks.
- Misconfigurations: These occur when security settings are not correctly configured, leaving systems vulnerable. Common examples include unsecured databases, default settings, or open cloud storage.
- Missing Encryption: Refers to the absence of encryption in data storage or transmission, making sensitive information susceptible to interception and unauthorized access.
- Malicious Insiders: Involves threats from individuals within the organization who abuse their access rights to steal or manipulate data for personal gain or to cause harm to the organization.
- Vulnerabilities: These are flaws or weaknesses in software and hardware that can be exploited by attackers to gain unauthorized access or cause harm. This includes everything from outdated software to unpatched security flaws.
- API Attacks: Attacks targeting the vulnerabilities in Application Programming Interfaces (APIs). These can include injection attacks, broken authentication, or exposure of sensitive data due to inadequate security measures.
Understanding these attack vectors is key to developing effective defense strategies. Each vector requires a different approach for mitigation, emphasizing the need for a diverse and multi-layered security strategy.
The Relationship Between Attack Surface and Attack Vectors
The interplay between attack surfaces and attack vectors is a critical aspect of cybersecurity. Understanding this relationship is essential for developing effective proactive strategies to secure your assets. Let’s explore some ways they are connected:
- Increased Attack Surface Leads to More Attack Vectors: A simple principle of cybersecurity is that the larger the attack surface, the more opportunities there are for potential attacks. Each component of your attack surface – be it a device, a piece of software, or a human element – can be targeted through different attack vectors. For instance, a large number of endpoints increases the chances of a successful phishing attack, while more applications can lead to a higher risk of software vulnerabilities being exploited.
- Specific Components, Specific Vectors: Different components of the attack surface are susceptible to specific attack vectors. For example:
- Web Applications: These are often targets for SQL Injections of cross-site scripting (XSS) attacks.
- Email Systems: A common entry point for phishing attacks
- Unpatched Software: This can be exploited through malware or zero-day attacks.
- Dynamic Nature of Attack Vectors: As the attack surface evolves with new technology and practices, so do the attack vectors, from phishing and social engineering to insider threats. The complexity and unpredictability of human behavior make this a challenging aspect to secure.
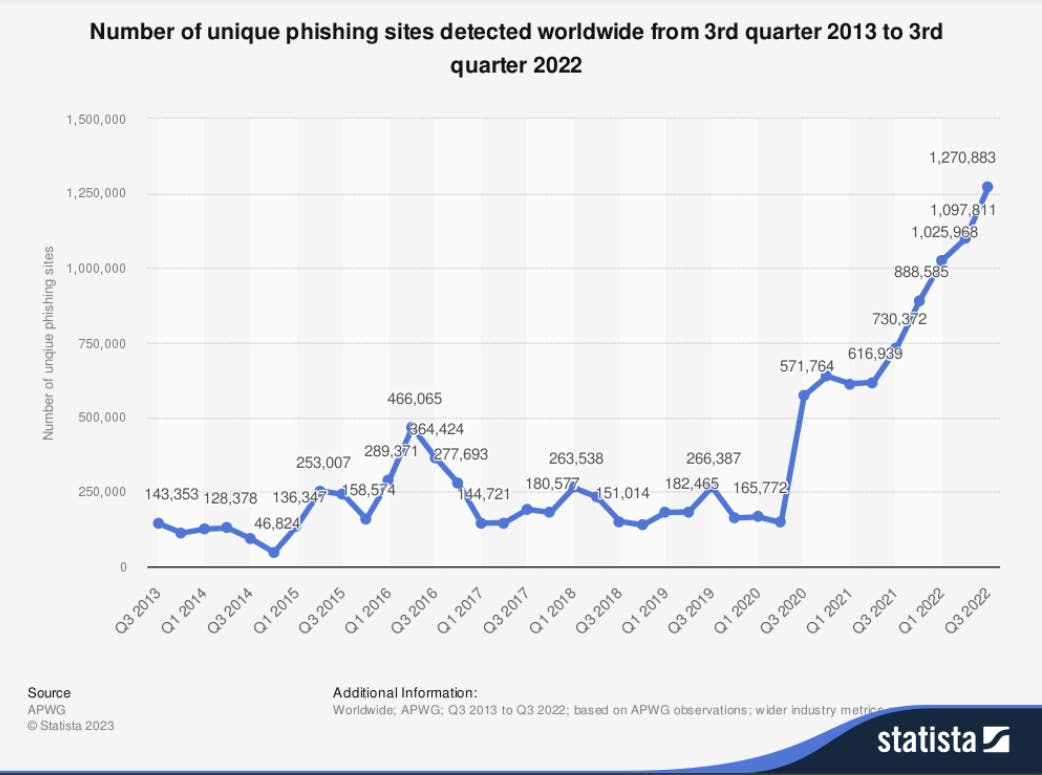
- The Human Factor: The human component of the attack surface is unique in its vulnerability to such a wide range of attack vectors. This can include phishing, social engineering, and insider threats. The complexity and unpredictability of human emotion and behavior make this one of the most challenging things to secure. If you have doubts about the scale of the human attack surface and attack vectors, look at this data from the Anti-Phishing Working Group (AWPG) published on Statista.
- Layered Defense Strategy: Understanding the relationship between your track surface and potential attack vectors allows for a more layered and comprehensive defense strategy. It’s not just about securing the perimeter. It is also about securing each layer and aspect of your network, systems, and people.
By understanding this relationship completely, organizations can better prepare for, respond to, and mitigate any risks they face. This approach is not about eliminating the attack surface or attack vectors, as this is an impossible task, but managing them in a way that greatly minimizes risk and impact.
How to Minimize Risk
Risk mitigation begins with the people that power your company. Investing in comprehensive cybersecurity awareness training for your employees can help to stave off most forms of phishing and similar social engineering schemes. However, this won’t completely stop attackers.
By leveraging the tactics below, you can minimize the risk your attack surface poses to your organization:
Downsize Your Attack Surface
You should always be on the lookout for opportunities to reel in the size and scope of your attack surface. Reducing complexity across your network is a great way to make it safer as a whole. This can be simplified to a large degree through network segmentation.
You may need to address any ports left open on critical devices within your network to secure it. It can also be advantageous to begin eliminating unused accounts, software, and entire devices wherever possible. In general, the more you can reduce the attack surface of your organization, the less likely it is that there will be common attack vectors to exploit in your environment.
Leverage the Right Tools
Continuous digital supply chain discovery can be an excellent means of acquiring intel on the assets your network currently contains. Any unknowns or rogue assets can then be dealt with appropriately.
You can also seek out tools for continuous attack surface discovery and vulnerability scanning. An Attack Surface Management (ASM) solution like IONIX can offer you the widest possible coverage, identifying assets within your network and evaluating them to streamline security.
Conclusion
Your organization’s attack surface encompasses all of the entry points and attack vectors hackers could use to gain access to your network. Each attack vector is a point at which bad actors can get in or a method by which they can set up their next malicious act. Knowing the common attack vectors that your organization may face, and how to mitigate them, is key for good security practice.
Securing your network is necessary, but it becomes more difficult as your attack surface expands. ASM solutions like IONIX offer continuous discovery, risk prioritization, and actionable remediation steps to eliminate attack vectors before they can negatively impact operations. Book a demo today to learn how IONIX can help you take a proactive approach to security.
Frequently Asked Questions
How can I minimize my attack surface?
Minimizing your attack surface involves reducing the potential points of vulnerability that an attacker can target. Here are some steps you can take:
- Regularly update and patch software to address known vulnerabilities.
- Disable unnecessary services, ports, and features on your systems.
- Implement strong access controls and least privilege principles to limit user access.
- Use network segmentation to isolate critical systems from less secure ones.
- Conduct regular security audits and vulnerability assessments to identify and address weaknesses.
How can I reduce the number of attack vectors?
Reducing attack vectors means limiting the ways in which an attacker can gain unauthorized access to your systems. Follow these practices:
- Keep software up-to-date to mitigate known vulnerabilities.
- Implement a robust firewall and intrusion detection/prevention systems.
- Use strong authentication mechanisms, such as multi-factor authentication (MFA).
- Regularly review and manage user permissions and access rights.
- Educate employees about phishing and social engineering to prevent human-related vulnerabilities.
What is the most common attack vector?
Phishing remains one of the most common attack vectors. Phishing involves using deceptive emails, messages, or websites to trick individuals into revealing sensitive information, such as login credentials or personal data. It is crucial to educate employees and users about recognizing and avoiding phishing attempts to safeguard against this prevalent attack vector.






