Is Gartner Waving ‘Bye Bye Bye’ to EASM?

New Gartner 2024 Hype Cycle plants EASM firmly in the “Trough of Disillusionment” and we couldn’t agree more.
TLDR: The ways that organizations find and fix security exposures have been flawed for years. Traditional vulnerability management (VM) programs have failed to address the core issues. What’s worse, the relatively new category of External Attack Surface Management (EASM) has not solved the problems it aimed to solve. But hope, in the form of Exposure Management, is on the way.
VM programs are commonplace in every entrprise security stack – looking at mostly known assets and using standards for finding vulnerabilities based on established CVE frameworks like MITRE and NIST. These tools provide a baseline for understanding and assessing vulnerabilities. But perhaps five years ago, the blind spots of these tools made way for a new crop of solutions, known as EASM platforms, that scan externally facing (web) assets (domains, FQDNs, IPs…) to cover the ever-growing, ever-changing, public-facing attack surface.
Using EASM tools, companies started to find 20% more (and sometimes even 50% more!) assets when looking from the “outside in” – and they started adding EASM platforms to their tooling faster than you could say “External Attack Surface Management”.
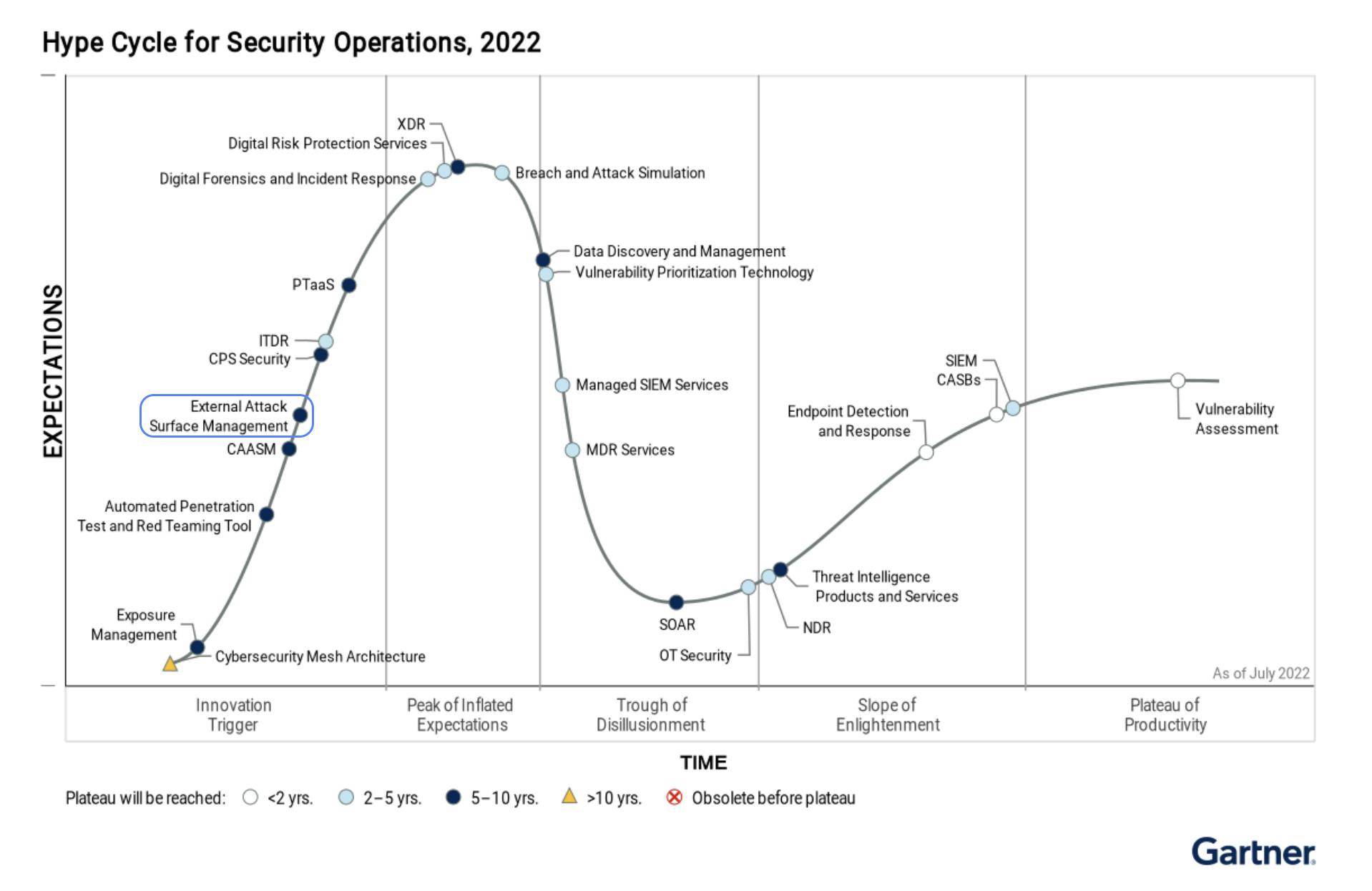
As the image from the 2022 Gartner Hype Cycle for Security Operations above shows, it took almost no time for EASM to become a visible, profitable category and move quickly up the “innovation trigger” section of the Hype Cycle. Like many nascent categories in the cybersecurity market – frenzied consolidation ensued. IBM bought Randori, Palo Alto bought Xpanse, Microsoft bought RiskIQ… and these EASM products quickly became part of larger offerings from the cyber behemoths. The EASM market was on fire, with many acquisitions and customers genuinely happy with the promise of greater attack surface visibility. By 2023, EASM had fully moved up to the Hype Cycle peak.
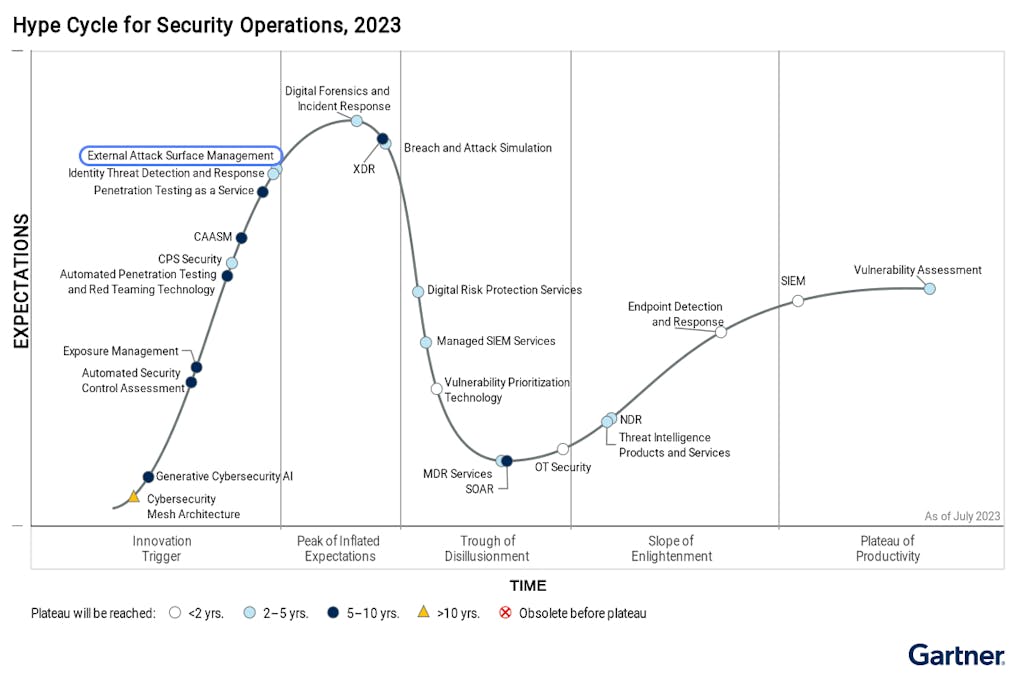
Unfortunately – that’s where promise of EASM started to fracture. As market consolidation happened, three things became clear:
- Visibility that came from the first generation of EASM tools was not good enough and still left blind spots. Plus, having too many false positives – assets mistakenly identified as belonging to a given customer – left customers frustrated.
- Companies with EASM continued to assess exposures incorrectly, leading to efforts being directed at fixing the wrong issues. This misdirection was a waste of resources and failed to mitigate the most critical risks.
- Visibility became yet another source of endless alerts – with no processes for operationalizing the noise, consolidating findings or integrating into existing tooling.
Fast forward to today – the just-released 2024 Gartner Hype Cycle for Security Operations and places EASM firmly in the “Trough of Disillusionment” stating one key reason as, “enterprises were unprepared to consume and operationalize service output [of] digital risk protection services, external attack surface management, and ITDR”. EASM, in its first incarnation, promised much and delivered little. The security findings from EASM tools could not be easily validated, routed to the right teams, or fixed quickly.
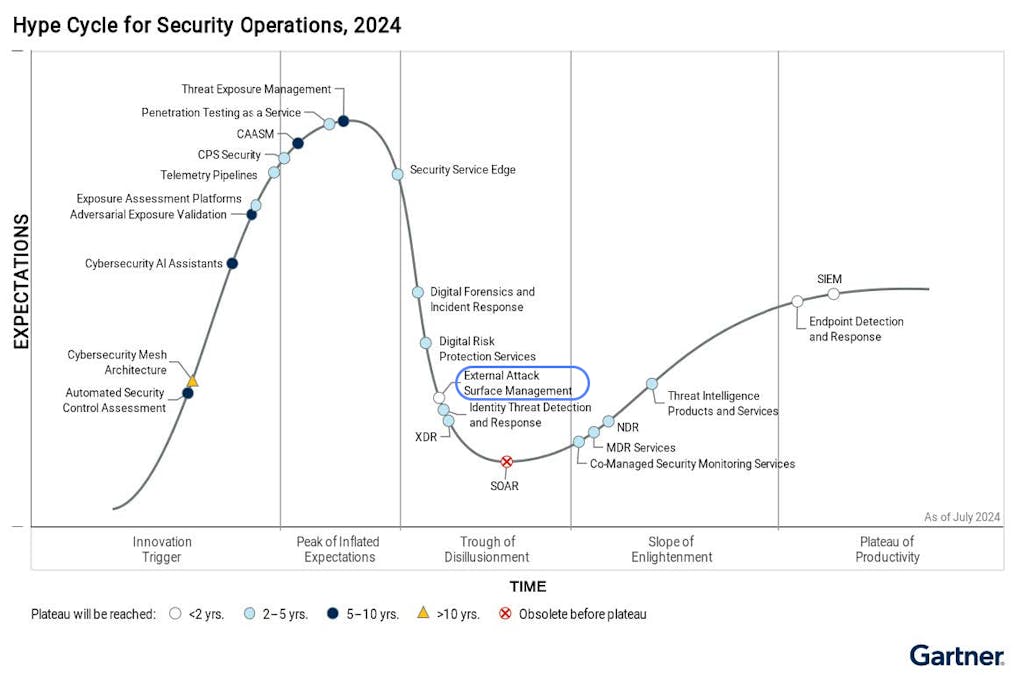
Enter Exposure Management: A New Hope

Recently, a new category has emerged, one that consolidates some of the promise of EASM together with solutions for the EASM failings – Exposure Management. Sometimes this is referred to as Continuous Threat Exposure Management (CTEM) or just TEM. The goal of exposure management is to shift focus from vulnerability to exploitability – to look for actual exposures rather than endless possible CVEs and misconfigurations.
What is Exposure Management?
The principles of cybersecurity Exposure Management focus on ensuring that organizations can effectively discover more, validate exposures to prioritize the right actions, and operationalize remediation and security findings. Here is a detailed explanation of each principle:
Wider Discovery: This involves knowing more about potential threats, vulnerabilities, and exposures but now with proof, context and asset importance taken into account. Discovery should include assets managed and owned by the organization, but also cloud assets, vendor-managed assets and even digital (or web) supply chain assets that are connected to an asset that belongs to the org. Discovery proof should show clear evidence of how assets are attributed to the org.
Validation and Prioritization: Once potential exposures are discovered, the next step is to validate these findings and prioritize them based on their true exposure and potential business impact. This approach ensures that exploitable assets are addressed first. Rather than merely creating an inventory of vulnerabilities, this principle advocates for a more dynamic understanding of how assets are connected, often represented as a graph, to better comprehend the relationships and impacts of security issues.
Operational Simplicity: Reducing the mean time to repair (MTTR) is vital for effective exposure management. This principle focuses on streamlining the process for resolving alerts and ensuring that they reach the right team. Providing easy-to-follow instructions for remediation helps IT teams act quickly and efficiently. Integrations with SIEM and ticketing systems ensure that security measures are implemented promptly and get to the right team, minimizing the window of opportunity for potential attackers.
These three principles move us from EASM, which was focused on discovery and asset inventories, to Exposure Management, which is focused on exploitability, validation and simplifying remediation operations across the attack surface.
Finally, a word about words 🙂
If all we do is shift terminology from EASM to EM or CTEM – we don’t help anyone. In my mind, EASM was a good start – it filled a real need and genuinely helped with visibility. But visibility is no longer enough. We owe it to the market to bring better tools that highlight actual exposures and that are built to simplify the operational aspects of remediation. The market shift to Exposure Management is a welcome one, and one that we at IONIX are proud to help customers manage every day.






