How to Prevent Credential Stuffing in 3 Steps (e.g. naz.API)

What is Credential Stuffing
Credential stuffing is a cyberattack method where attackers use lists of compromised user credentials to breach into a system. These credentials, often obtained from previous data breaches and available on various dark web forums, include combinations of usernames, email addresses, and passwords.
Credential stuffing attacks – how does it work?
Credential stuffing attacks operate on the premise that people often reuse their passwords on different websites and services. Armed with a list of compromised credentials, these attacks target multiple websites or services in an attempt to gain unauthorized access. They leverage automated tools to try thousands to millions of credential combinations in a short period.
What is naz.API credential stuffing list?
The term naz.API is a mega credential stuffing list. It has gained notoriety among digital privacy and cybersecurity professionals due to its massive size and the number of previously unseen on the dark web credentials.
Naz.API credential stuffing list in numbers:
- 319 files totaling 104GB of data
- Around 71M unique email addresses
- Overall 1B rows of username/password pairs along with their related domain
- Over 35% of the email addresses were not previously seen on the Have I Been Pwned website.
The data found in the naz.API data set appears to have been compiled from credential stuffing lists and from information-stealing malware logs. It is important to mention that this unprecedented quantity of leaked credentials is not the result of a single breach but rather a compiled collection of multiple data leaks generated on multiple occasions.
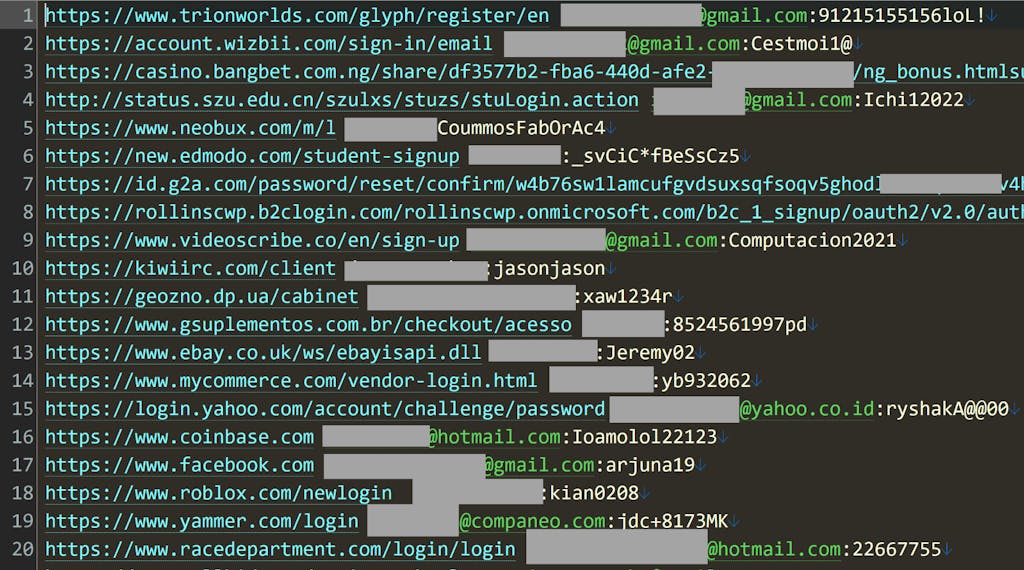
Figure 1 – Source – troyhunt.com
Awareness of the naz.API list rose following a blog published in the well-known illicit.services OSINT platform. Later, the data was also pushed to the popular service – Have I Been Pwned (HIBP) website This massive credential stuffing list created waves of confusion, causing organizations around the world to initiate global investigations into the potential impact to their core data and in turn – their reputation.
Credential stuffing vs data extraction attacks
Credential stuffing attacks are based on data gathered from Information-stealing malware attempts to steal a wide variety of data from an infected computer, including credentials saved in browsers, VPN clients, and FTP clients. This type of malware also attempts to steal SSH keys, credit cards, cookies, browsing history, and cryptocurrency wallets.

Figure 2 – Stealer Log Example (troyhunt.com)
The common opinion is that infostealers-generated credential data is more reliable since it reflects the actual keystrokes the user entered during the login session along with the login page where these credentials have been used.
Data breaches may extract substantial amounts of data but lack context and usually refer to a single system user repository. This data may also be used later to create credential-stuffing lists, assuming many users reuse passwords through different, unrelated services – exposing a single infostealer “tested” login data to an endless number of services.
Prevent credential stuffing attacks in 3 steps
Preventing or at least reducing future naz.API and other infostealers leaks is not easy but is achievable with several steps for both IT and the compromised services:
- Make sure AV and Web Protection tools are installed and are correctly configured. These include device software such as AV and other web protection tools and can be extended to DLP and other infrastructure data-oriented security tools which can “sniff” and block traffic while it is being transmitted out of the organization or identify destination IPs which belongs to known malicious Control-and-Command centers (C&C) using 3rd party threat intelligence services in order to block all outgoing traffic towards these services.
- Embed an organization password manager to reduce password reuse chances. This will reduce a potential breach to a single service at a time.
- Embed Two-factor-authentication (2FA) to all service login processes to reduce the chances of service login once a device is compromised and credentials are leaking.
What does not help to prevent Credential Stuffing attacks?
Password complexity is irrelevant in the case of infostealers. While a strong password may help preventing brute-force access, an infostealer captures whatever password the user is typing – revealing the password, despite its complexity.
Mitigate credential stuffing attacks risks in your organization
In the previous section, I discussed 3 prevention steps. Now, lets take a look at an addtional mitigation approach that can dramatically reduce the risk of a successful credential stuffing attack on your organizations.
First let’s face the facts.
Credential stuffing lists regularly appear on the deep and dark web. While the data gathered into the naz.API dataset was unique in size and freshness, it is not the first list and most probably not the last.
To mitigate risk of credential stuffing attacks on the organizations IT infrastructure, security teams need to combine visibility; know their inventory using continuous attack surface discovery and identify the latest relevant mentions regarding leaked credentials and compromised machines with threat intelligence from the deep and dark web. This process can be automated using an advanced attack surface management platform like IONIX ASM.
IONIX integrates threat intelligence feeds into it’s attack surface management platform. This integration enables organizations to
- Scan through employee and user leaked credentials based on date of leak – pointing them to the most recent (and in most cases, validated) events
- Identify compromised devices in their asset inventory and remediate those to prevent future credential leaks.
- Correlate leaked credentials access to assets in your inventory, including login pages.
Summary
In summary, understanding and combating credential stuffing is critical in today’s digital landscape. The naz.API list served as a wakeup call about such threats to organizational security.
By adhering to three key steps—enhancing antivirus and web protection, utilizing password managers, and implementing two-factor authentication—organizations can significantly mitigate the risk of these attacks. However, to truly fortify your defenses against the evolving tactics of cybercriminals, leveraging attack surface management platforms, like IONIX, that integrate threat intelligence feeds. This offers a proactive approach to identifying and mitigating risks posed by compromised credentials and devices. To see IONIX in action, request a scan today.






