What is the CIS Controls Framework?
The Center for Internet Security (CIS) Controls framework provides a collection of defense-in-depth best practices designed to mitigate the most common cyber attacks on systems and networks. Each Control set outlines specific actions, known as safeguards, that organizations can implement to strengthen their security posture.
In this article
These actions are prioritized into Implementation Group (IG) based on their complexity and resource requirements.
The latest version, 8.1, includes eighteen critical security Controls and is an iterative update from version 8.0, with enhancements focused on improving context, clarity and consistency.
The Origin of CIS Controls
The CIS Controls are developed and maintained by a global community of volunteers and institutions dedicated to studying cyber attacks, identifying their root causes and translating those insights into actionable defenses. Originally based on publicly available lists of attacks, the CIS Controls have evolved and adopted a data-driven approach, using breach investigation reports and large-scale data analysis to inform their guidelines.
CIS Benchmarks
In addition to the CIS Controls, CIS Benchmarks provide separate, detailed recommendations for securely configuring over 25 vendor product families. While the CIS Controls offer general, vendor-agnostic security strategies, the Benchmarks specify configurations for individual products.
Together, these resources make up the CIS Security Best Practices – a comprehensive, prescriptive and prioritized set of actions supported by a community network. This combination ensures that the practices are implementable, usable, scalable and aligned with industry and government security requirements.
CIS Controls vs NIST CSF
The National Institute of Standards and Technology Cyber Security Framework (NIST CSF) is another publication that provides guidance for managing cybersecurity risks across a variety of organizations. It outlines high-level cybersecurity related outcomes, grouped into six main Functions: Govern, Identify, Protect, Detect, Respond and Recover.
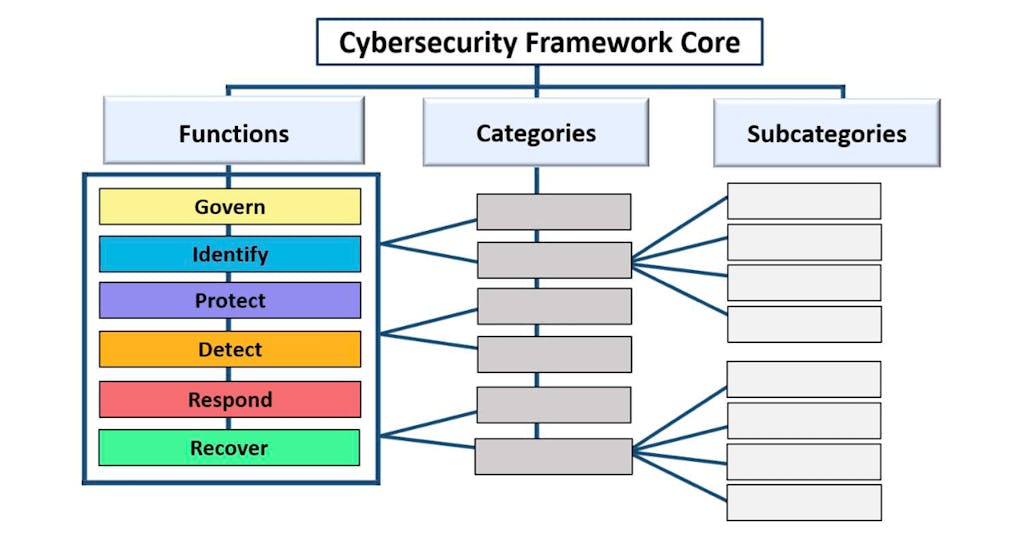
The key distinction between the CIS Controls and the NIST CSF lies in their focus. CIS Controls are task-driven, defining specific steps that organizations can take to enhance their security posture. In contrast, the NIST CSF is outcome-driven, focusing on achieving broad security goals and providing a framework for assessing overall effectiveness. Essentially, the CIS Controls detail specific steps and the NIST CSF emphasizes the desired results of those steps.

Despite being distinct, the CIS Controls incorporate aspects of the NIST CSF to align with industry standards. The CIS Controls have been updated to reflect NIST CSF 2.0, mapping each CIS Control sub-category to a corresponding NIST Security Function.
The 18 Controls
Below is a list of all eighteen CIS Controls along with their official descriptions. Each Control is further explored in a detailed blog post that provides an in-depth look at its significance, coverage and the associated Implementation Groups.
- Inventory and Control of Enterprise Assets
Actively manage (inventory, track and correct) all enterprise assets (end-user devices, including portable and mobile; network devices; non-computing/Internet of Things (IoT) devices; and servers) connected to the infrastructure, physically, virtually, remotely and those within cloud environments, to accurately know the totality of assets that need to be monitored and protected within the enterprise. This will also support identifying unauthorized and unmanaged assets to remove or remediate.
- Inventory and Control of Software Assets
Actively manage (inventory, track and correct) all software (operating systems and applications) on the network so that only authorized software is installed and can execute and that unauthorized and unmanaged software is found and prevented from installation or execution.
- Data Protection
Develop processes and technical Controls to identify, classify, securely handle, retain and dispose of data.
- Secure Configuration of Enterprise Assets and Software
Establish and maintain the secure configuration of enterprise assets (end-user devices, including portable and mobile, network devices, non-computing/IoT devices and servers) and software (operating systems and applications).
- Account Management
Use processes and tools to assign and manage authorization to credentials for user accounts, including administrator accounts, as well as service accounts to enterprise assets and software.
- Access Control Management
Use processes and tools to create, assign, manage and revoke access credentials and privileges for user, administrator and service accounts for enterprise assets and software.
- Continuous Vulnerability Management
Develop a plan to continuously assess and track vulnerabilities in all enterprise assets within the enterprise’s infrastructure in order to remediate and minimize the window of opportunity for attackers. Monitor public and private industry sources for new threats and vulnerability information.
- Audit Log Management
Collect, alert, review and retain audit logs of events that could help detect, understand or recover from an attack.
- Email and Web Browser Protections
Improve protections and detections of threats from email and web vectors, as these are opportunities for attackers to manipulate human behavior through direct engagement.
- Malware Defenses
Prevent or control the installation, spread and execution of malicious applications, code or scripts on enterprise assets.
- Data Recovery
Establish and maintain data recovery practices sufficient to restore in-scope enterprise assets to a pre-incident and trusted state.
- Network Infrastructure Management
Establish, implement and actively manage (track, report, correct) network devices, in order to prevent attackers from exploiting vulnerable network services and access points.
- Network Monitoring and Defense
Operate processes and tooling to establish and maintain comprehensive network monitoring and defense against security threats across the enterprise’s network infrastructure and user base.
- Security Awareness and Skills Training
Establish and maintain a security awareness program to influence behavior among the workforce to be security conscious and properly skilled to reduce cybersecurity risks to the enterprise.
- Service Provider Management
Develop a process to evaluate service providers who hold sensitive data or are responsible for an enterprise’s critical IT platforms or processes to ensure these providers are protecting those platforms and data appropriately.
- Application Software Security
Manage the security life cycle of in-house developed, hosted or acquired software to prevent, detect and remediate security weaknesses before they can impact the enterprise.
- Incident Response Management
Establish a program to develop and maintain an incident response capability (e.g., policies, plans, procedures, defined roles, training and communications) to prepare, detect and quickly respond to an attack.
- Penetration Testing
Test the effectiveness and resiliency of enterprise assets through identifying and exploiting weaknesses in Controls (people, processes and technology) and simulating the objectives and actions of an attacker.
Implementation Groups (IGs)
As previously mentioned, Implementation Groups are utilized to assign a priority level to a safeguard based on their implementation complexity. There are three levels of Implementation Groups: IG1, IG2 and IG3.
These IGs correspond to different levels of protection, with IG1 representing the most fundamental security measures and IG3 offering the most advanced protection. High-level IGs encompass the requirements of lower-level ones, meaning that any safeguard required at IG1 must also be implemented at IG2 and IG3 levels.
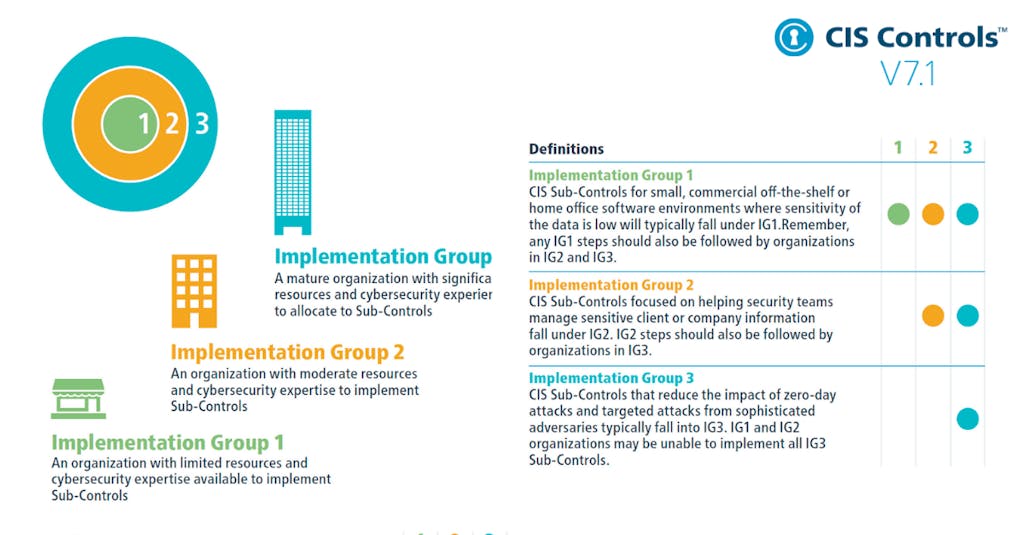
IG1
IG1 is the most basic implementation group, consisting only of safeguards to implement “essential cyber hygiene“. An IG1 enterprise is small to medium-sized with limited IT and cybersecurity expertise to dedicate toward protecting IT assets and personnel. The principal concern of these enterprises is to keep the business operational, as they have a limited tolerance for downtime.
The sensitivity of the data that they are trying to protect is low and principally surrounds employee and financial information. Safeguards selected for IG1 should be implementable with limited cybersecurity expertise and aimed to thwart general, non-targeted attacks.
IG2
IG2 is the next complexity level up and includes all Controls in IG1. An IG2 enterprise employs individuals responsible for managing and protecting IT infrastructure. These enterprises support multiple departments with differing risk profiles based on job function and mission. Small enterprise units may have regulatory compliance burdens.
IG2 enterprises often store and process sensitive client or enterprise information and can withstand short interruptions of service. A major concern is the loss of public confidence in the event of a breach.
IG3
This is the final level and includes both IG1 and IG2. An IG3 enterprise employs security experts that specialize in the different facets of cybersecurity (e.g., risk management, penetration testing, application security). IG3 assets and data contain sensitive information or functions that are subject to regulatory and compliance oversight.
An IG3 enterprise must address availability of services and the confidentiality and integrity of sensitive data. Successful attacks can cause significant harm to the well-being of the public. Safeguards selected for IG3 must be capable of defending against targeted attacks from a sophisticated adversary and reducing the impact of zero-day attacks.
Which Controls are the Most Crucial to Implement?
With a multitude of CIS Controls to choose from and constraints such as limited budgets, time and varying skill levels within security teams, prioritization is crucial. While implementing all the Controls for a chosen Implementation Group (e.g., all of IG1) offers the most comprehensive security, practical limitations often require a more focused approach. Therefore, it’s essential to prioritize the following key Controls to effectively enhance your security posture:
Data Recovery (Control 11)
The primary aim of cybersecurity is to safeguard the organization’s business and mission. Since no business is immune to all cyber risks, data recovery and business continuity should be your top priorities. Effective data recovery measures act as a safety net, ensuring that your organization can recover and continue operations when security breaches or failures occur.
Inventory and Control of Enterprise and Software Assets (Control 1 & 2)
Protection cannot be provided to assets you are unaware of. Therefore, maintaining an inventory of both enterprise hardware and software assets is crucial. This includes all assets connected physically, virtually, remotely and those within cloud environments. Identifying the data and assets that are most critical to your organization enables you to apply appropriate security measures. Additionally, having an inventory of software assets allows you to implement an allowlist of authorized applications, which is an effective strategy to prevent malware and unauthorized software execution.
Access Control Management (Control 6)
With the increase in info-stealer malware and the sale of plaintext credentials on the dark web, many breaches can be traced back to inadequate access control. Effective access control management involves establishing processes to grant and revoke access, enforcing multi-factor authentication (MFA) and centralizing access through technologies like Single Sign-On (SSO) whenever it is possible.
Continuous Vulnerability Management (Control 7)
Externally accessible systems are common targets. Malicious attackers constantly scan the internet for vulnerabilities to exploit. Organizations that fail to assess and address vulnerabilities in their infrastructure are at a higher risk of compromise. A continuous vulnerability management plan helps identify and remediate vulnerabilities swiftly, reducing the window of opportunity for attacker


