CIS Control 10 Explained: Malware Defenses
CIS Control 10 involves malware defenses. This means to prevent or control the installation, spread and execution of malicious applications, code or scripts on enterprise assets.
In this article
The Importance of Control 10
Malware can infect enterprise assets through various channels, including web browsing, compromised cloud servers, drive-by downloads, email phishing, malicious software dependencies and physical media like Universal Serial Bus (USB) drives and compact discs (CD). Threats like infostealers and ransomware can cause significant damage to an organization, even from just one compromised endpoint. To protect against the execution of malicious code, it is vital to maintain up-to-date anti-malware defenses across all potential entry points.
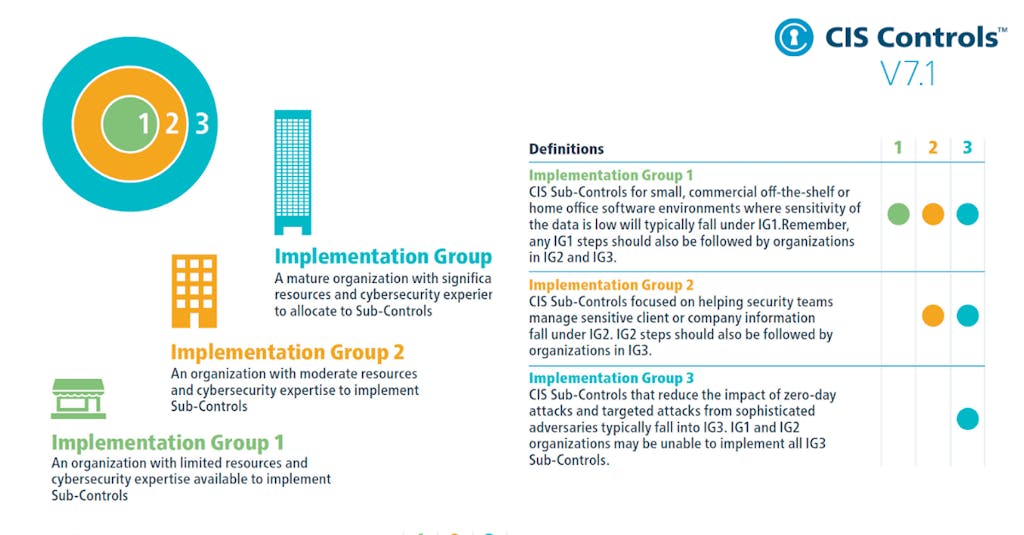
Implementation Groups (IGs)
To implement CIS Controls, follow each listed safeguard, which details the required activities. Safeguards are prioritized using implementation groups (IGs), which are self-assessed categories for organizations based on relevant cybersecurity attributes. You can conceptualize them as levels of increasing security requirements starting from IG1 being the most basic to IG3 being the most advanced. The higher level groups are included in the lower ones.
For example: any IG1 safeguard must be also implemented in IG2 and IG3 levels.
The Safeguards of Control 10
There are seven safeguards in CIS Control 10. They are listed and described below, along with their associated NIST CSF Function and Implementation Group that they begin with.
| Safeguard Number | Safeguard Title | NIST Security Function | StartingImplementation Group |
| Safeguard 10.1 | Deploy and Maintain Anti-Malware Software | Detect | IG1 |
| Safeguard 10.2 | Configure Automatic Anti-Malware Signature Updates | Protect | IG1 |
| Safeguard 10.3 | Disable Autorun and Autoplay for Removable Media | Protect | IG1 |
| Safeguard 10.4 | Configure Automatic Anti-Malware Scanning of Removable Media | Detect | IG2 |
| Safeguard 10.5 | Enable Anti-Exploitation Features | Protect | IG2 |
| Safeguard 10.6 | Centrally Manage Anti-Malware Software | Protect | IG2 |
| Safeguard 10.7 | Use Behavior-Based Anti-Malware Software | Detect | IG2 |


