CIS Control 12 Explained: Network Infrastructure Management
CIS Control 12 involves network infrastructure management – to actively manage (track, report, correct) network devices. Network infrastructure includes devices such as physical and virtualized gateways, firewalls, wireless access points, routers and switches.
In this article
The Importance of Control 12
Secure network infrastructure is vital for defending against attacks. This involves establishing a robust security architecture that addresses vulnerabilities from default settings, along with ongoing monitoring and regular configuration assessments.
Default configurations for network devices often prioritize convenience over security, creating vulnerabilities such as open services and ports, default accounts and passwords (including for services), outdated protocols and unnecessary pre-installed software. Attackers target these weaknesses and gaps in firewall rules, routers and switches and then exploit them to breach defenses, access networks, redirect traffic and intercept data during transmission.
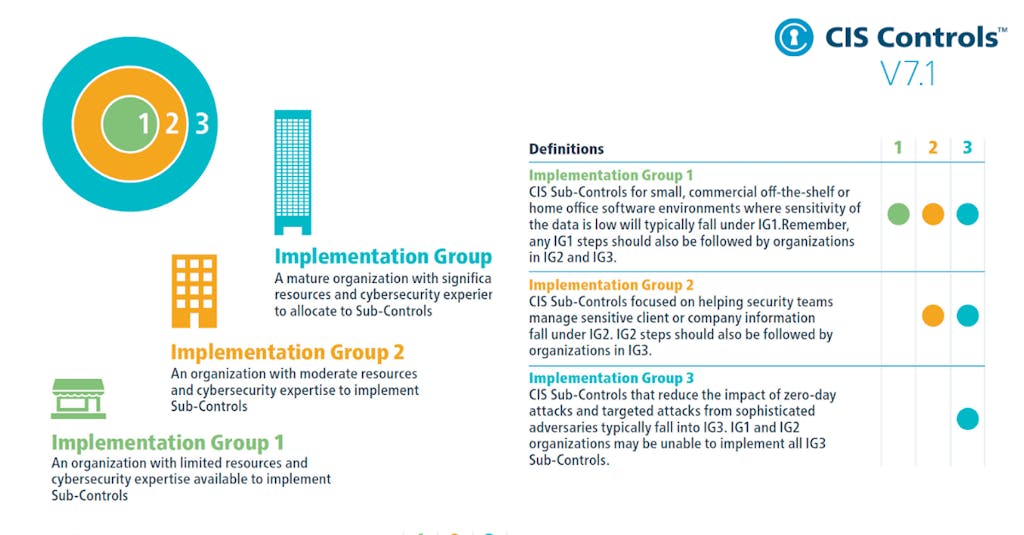
Implementation Groups (IGs)
To implement CIS Controls, follow each listed safeguard, which details the required activities. Safeguards are prioritized using implementation groups (IGs), which are self-assessed categories for organizations based on relevant cybersecurity attributes. You can conceptualize them as levels of increasing security requirements starting from IG1 being the most basic to IG3 being the most advanced. The higher level groups are included in the lower ones.
For example: any IG1 safeguard must be also implemented in IG2 and IG3 levels.
The Safeguards of Control 12
There are eight safeguards in CIS Control 12. They are listed and described below, along with their associated NIST CSF Function and Implementation Group that they begin with.
| Safeguard Number | Safeguard Title | NIST Security Function | StartingImplementation Group |
| Safeguard 12.1 | Ensure Network Infrastructure is Up-to-Date | Protect | IG1 |
| Safeguard 12.2 | Establish and Maintain a Secure Network Architecture | Recover | IG1 |
| Safeguard 12.3 | Securely Manage Network Infrastructure | Protect | IG2 |
| Safeguard 12.4 | Establish and Maintain Architecture Diagram(s) | Govern | IG2 |
| Safeguard 12.5 | Centralize Network Authentication, Authorization and Auditing (AAA) | Protect | IG2 |
| Safeguard 12.6 | Use of Secure Network Management and Communication Protocols | Protect | IG2 |
| Safeguard 12.7 | Ensure Remote Devices Utilize a VPN and are Connecting to an Enterprise’s AAA Infrastructure | Protect | IG2 |
| Safeguard 12.8 | Establish and Maintain Dedicated Computing Resources for All Administrative Work | Protect | IG3 |


