CIS Control 13 Explained: Network Monitoring and Defense
CIS Control 13 involves network monitoring and defense – meaning to use processes and tools to establish and maintain comprehensive network monitoring and defense against security threats across the enterprise’s network infrastructure and user base.
In this article
The Importance of Control 13
Enterprises often remain compromised for weeks, months or even years before detection. Comprehensive situational awareness allows for quicker detection and response, which is vital for minimizing the impact of malware, credential theft or data breaches.
Effective situational awareness, supported by robust security operations, helps enterprises identify and catalog attackers’ Tactics, Techniques and Procedures (TTPs) and their Indicators of Compromise (IOCs). This proactive approach enables better anticipation of future threats. Moreover, having complete information about the environment and enterprise structure accelerates recovery and allows for the development of efficient response strategies.
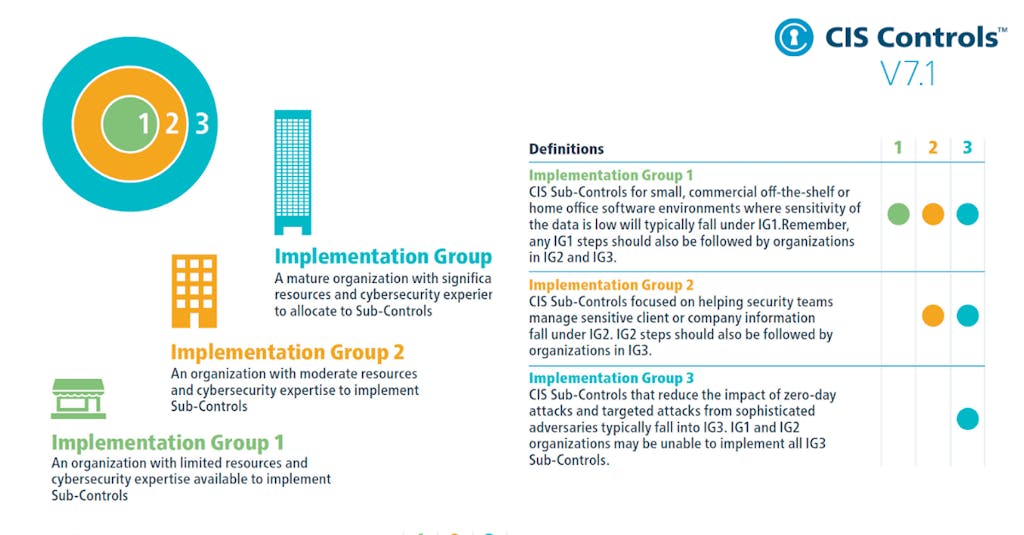
Implementation Groups (IGs)
To implement CIS Controls, follow each listed safeguard, which details the required activities. Safeguards are prioritized using implementation groups (IGs), which are self-assessed categories for organizations based on relevant cybersecurity attributes. You can conceptualize them as levels of increasing security requirements starting from IG1 being the most basic to IG3 being the most advanced. The higher level groups are included in the lower ones.
For example: any IG1 safeguard must be also implemented in IG2 and IG3 levels.
The Safeguards of Control 13
There are eleven safeguards in CIS Control 13. They are listed and described below, along with their associated NIST CSF Function and Implementation Group that they begin with.
| Safeguard Number | Safeguard Title | NIST Security Function | StartingImplementation Group |
| Safeguard 13.1 | Ensure Network Infrastructure is Up-to-Date | Detect | IG2 |
| Safeguard 13.2 | Deploy a Host-Based Intrusion Detection Solution | Detect | IG2 |
| Safeguard 13.3 | Deploy a Network Intrusion Detection Solution | Detect | IG2 |
| Safeguard 13.4 | Perform Traffic Filtering Between Network Segments | Protect | IG2 |
| Safeguard 13.5 | Manage Access Control for Remote Assets | Protect | IG2 |
| Safeguard 13.6 | Collect Network Traffic Flow Logs | Detect | IG2 |
| Safeguard 13.7 | Deploy a Host-Based Intrusion Prevention Solution | Protect | IG3 |
| Safeguard 13.8 | Deploy a Network Intrusion Prevention Solution | Protect | IG3 |
| Safeguard 13.9 | Deploy Port-Level Access Control | Protect | IG3 |
| Safeguard 13.10 | Perform Application Layer Filtering | Protect | IG3 |
| Safeguard 13.11 | Tune Security Event Alerting Thresholds | Detect | IG3 |


