CIS Control 15 Explained: Service Provider Management
CIS Control 15 involves service provider management. That means to establish a process to evaluate service providers who hold sensitive data or are responsible for critical IT operations and ensure that they are protecting the availability, confidentiality and integrity of your organization’s information appropriately.
In this article
The Importance of Control 15
Many businesses today rely on third-party service providers for essential functions, such as data processing, operations and cybersecurity management. Breaches at these providers can lead to significant consequences for enterprises. Such incidents can disrupt operations and, in some cases, allow attackers to compromise data on a business’s systems by exploiting access through these providers. Therefore, managing third-party risks is critical to maintaining a secure business environment.
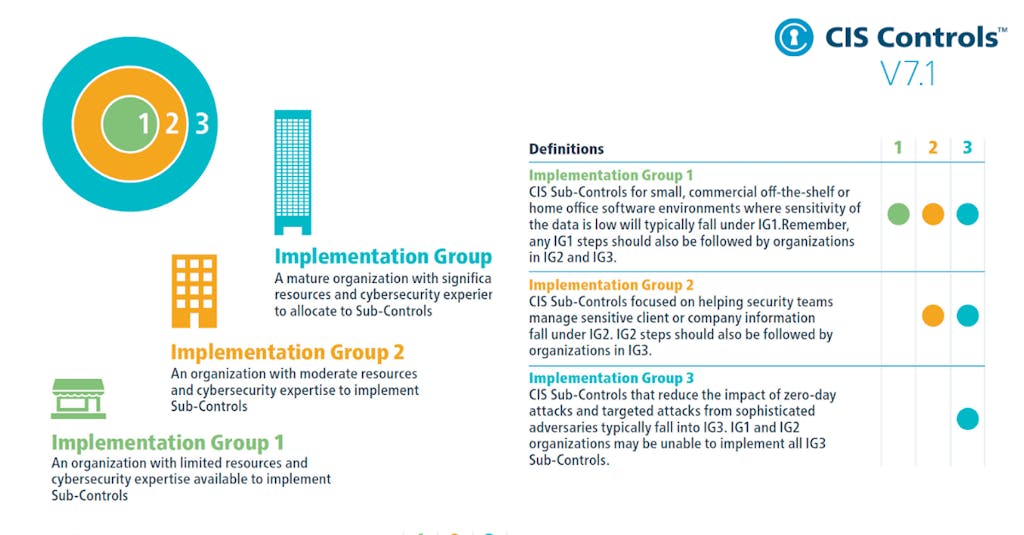
Implementation Groups (IGs)
To implement CIS Controls, follow each listed safeguard, which details the required activities. Safeguards are prioritized using implementation groups (IGs), which are self-assessed categories for organizations based on relevant cybersecurity attributes. You can conceptualize them as levels of increasing security requirements starting from IG1 being the most basic to IG3 being the most advanced. The higher level groups are included in the lower ones.
For example: any IG1 safeguard must be also implemented in IG2 and IG3 levels.
The Safeguards of Control 15
There are seven safeguards in CIS Control 15. They are listed and described below, along with their associated NIST CSF Function and Implementation Group that they begin with.
| Safeguard Number | Safeguard Title | NIST Security Function | StartingImplementation Group |
| Safeguard 15.1 | Establish and Maintain an Inventory of Service Providers | Identify | IG1 |
| Safeguard 15.2 | Establish and Maintain a Service Provider Management Policy | Govern | IG2 |
| Safeguard 15.3 | Classify Service Providers | Govern | IG2 |
| Safeguard 15.4 | Ensure Service Provider Contracts Include Security Requirements | Govern | IG2 |
| Safeguard 15.5 | Assess Service Providers | Govern | IG3 |
| Safeguard 15.6 | Monitor Service Providers | Govern | IG3 |
| Safeguard 15.7 | Securely Decommission Service Providers | Protect | IG3 |


