CIS Control 18 Explained: Penetration Testing
CIS Control 18 involves penetration testing. Penetration testing is a process to test the effectiveness and resiliency of enterprise assets through identifying and exploiting weaknesses in Controls (people, processes and technology) and simulating the objectives and actions of an attacker.
In this article
The Importance of Control 18
A successful defensive posture requires a comprehensive program that includes effective policies, robust technical defenses and appropriate human actions. However, achieving perfection is rare. In a complex and evolving technological landscape, enterprises should periodically test their controls to identify gaps and assess resilience. Testing can cover various aspects, including external and internal networks, applications, systems and even social engineering campaigns to test user awareness and physical access controls.
Independent penetration testing provides valuable, objective insights into vulnerabilities in enterprise assets and human factors, as well as the effectiveness of defenses. These tests are essential for ongoing security management and improvement, revealing process weaknesses like inconsistent configuration management and gaps in end-user training.
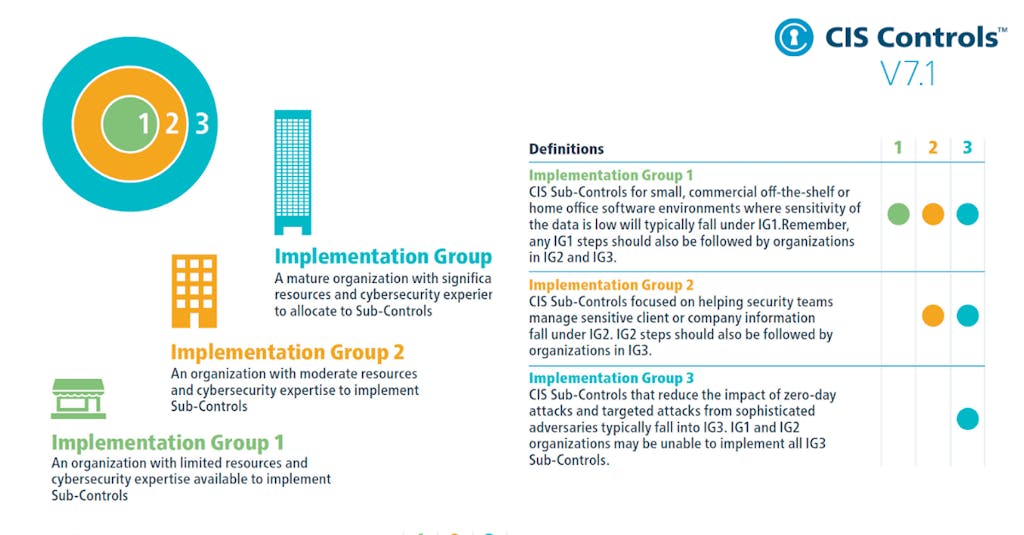
Implementation Groups (IGs)
To implement CIS Controls, follow each listed safeguard, which details the required activities. Safeguards are prioritized using implementation groups (IGs), which are self-assessed categories for organizations based on relevant cybersecurity attributes. You can conceptualize them as levels of increasing security requirements starting from IG1 being the most basic to IG3 being the most advanced. The higher level groups are included in the lower ones.
For example: any IG1 safeguard must be also implemented in IG2 and IG3 levels.
Penetration testing is typically only done by organizations above a baseline level of security maturity and with a moderate amount of security resources, so all items in CIS Control 18 start from IG2.
The Safeguards of Control 18
There are five safeguards in CIS Control 18. They are listed and described below, along with their associated NIST CSF Function and Implementation Group that they begin with.
| Safeguard Number | Safeguard Title | NIST Security Function | StartingImplementation Group |
| Safeguard 18.1 | Establish and Maintain a Penetration Testing Program | Govern | IG2 |
| Safeguard 18.2 | Perform Periodic External Penetration Tests | Detect | IG2 |
| Safeguard 18.3 | Remediate Penetration Test Findings | Protect | IG2 |
| Safeguard 18.4 | Validate Security Measures | Protect | IG3 |
| Safeguard 18.5 | Perform Periodic Internal Penetration Tests | Detect | IG3 |


