CIS Control 2 Explained: Inventory and Control of Software Assets
CIS Control 2 focuses on maintaining a comprehensive and current inventory of all software assets. This involves actively managing and monitoring all software on the network to ensure that only authorized applications and their correct versions are used. It’s essential to prevent the installation or execution of any unauthorized software. Additionally, keep all software updated with the latest patches and remove any unnecessary programs to maintain a secure environment.
In this article
The Importance of Control 2
Malicious attackers are constantly scanning enterprises for software versions with known vulnerabilities that can be remotely exploited.
Malware can be installed using malicious websites or attachments. Once installed, it can provide backdoor access to systems, resulting in long-term compromise. Attackers with such a foothold into a system can also use it to move throughout the network.
By upkeeping a reliable inventory of all software utilized, your organization will have better monitoring insights.
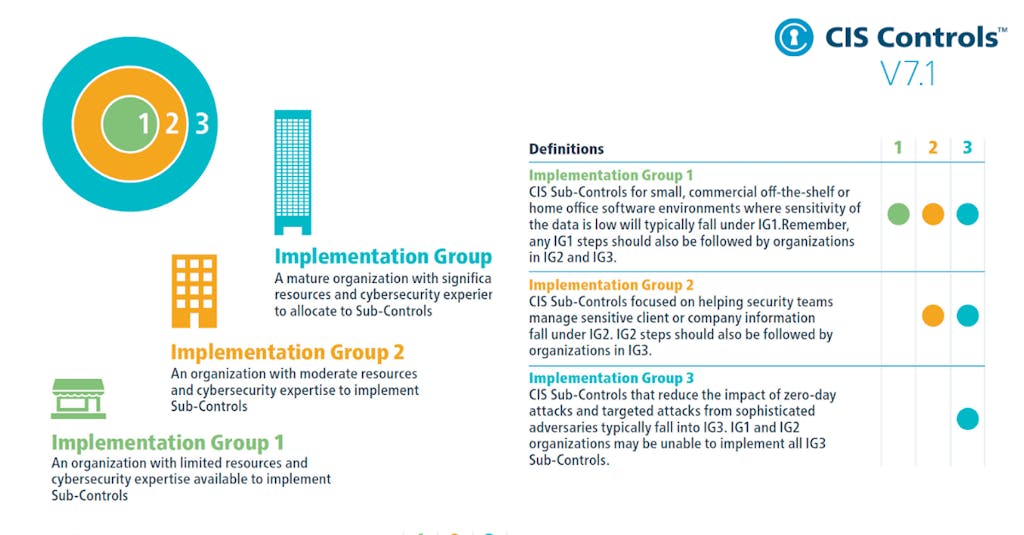
Implementation Groups (IGs)
To implement CIS Controls, follow each listed safeguard, which details the required activities. Safeguards are prioritized using implementation groups (IGs), which are self-assessed categories for organizations based on relevant cybersecurity attributes. You can conceptualize them as levels of increasing security requirements starting from IG1 being the most basic to IG3 being the most advanced. The higher level groups are included in the lower ones.
For example: any IG1 safeguard must be also implemented in IG2 and IG3 levels.
The Safeguards of Control 2
There are seven safeguards in CIS Control 2. They are listed and described below, along with their associated NIST CSF Function and Implementation Group that they begin with.
| Safeguard Number | Safeguard Title | NIST Security Function | StartingImplementation Group |
| Safeguard 2.1 | Establish and Maintain a Software Inventory | Identify | IG1 |
| Safeguard 2.2 | Ensure Authorized Software is Currently Supported | Identify | IG1 |
| Safeguard 2.3 | Address Unauthorized Software | Respond | IG1 |
| Safeguard 2.4 | Utilize Automated Software Inventory Tools | Detect | IG2 |
| Safeguard 2.5 | Allowlist Authorized Software | Protect | IG2 |
| Safeguard 2.6 | Allowlist Authorized Libraries | Protect | IG2 |
| Safeguard 2.7 | Allowlist Authorized Scripts | Protect | IG3 |


