CIS Control 5 Explained: Account Management
CIS Control 5 involves account management. This means using tools and processes to assign and manage credentials and access for user accounts for all enterprise assets and software.
In this article
The Importance of Control 5
Unauthorized access to enterprise assets or data is often easier for malicious attackers when they use valid user credentials rather than exploiting system vulnerabilities. There are various ways to gain access to user accounts such as brute forcing weak passwords, using social engineering tactics to trick users into revealing their credentials and malware designed to capture passwords or tokens in memory or over the network.
Administrative and highly privileged accounts are particularly attractive targets, as they enable attackers to create new accounts or make changes that could expose assets to further risks. Service accounts are also sensitive and are often shared among both internal and external teams.
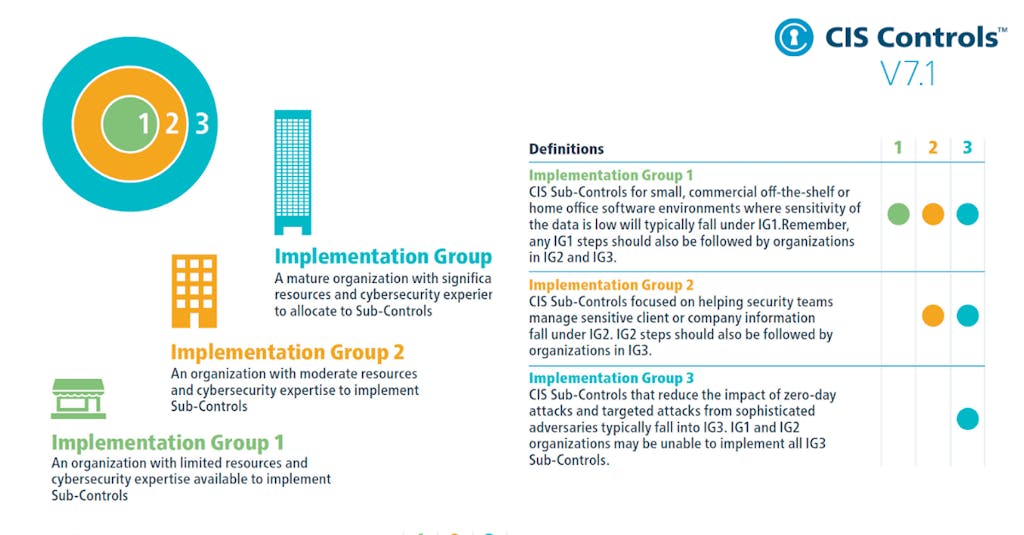
Implementation Groups (IGs)
To implement CIS Controls, follow each listed safeguard, which details the required activities. Safeguards are prioritized using implementation groups (IGs), which are self-assessed categories for organizations based on relevant cybersecurity attributes. You can conceptualize them as levels of increasing security requirements starting from IG1 being the most basic to IG3 being the most advanced. The higher level groups are included in the lower ones.
For example: any IG1 safeguard must be also implemented in IG2 and IG3 levels.
The Safeguards of Control 5
There are six safeguards in CIS Control 5. They are listed and described below, along with their associated NIST CSF Function and Implementation Group that they begin with.
| Safeguard Number | Safeguard Title | NIST Security Function | StartingImplementation Group |
| Safeguard 5.1 | Establish and Maintain an Inventory of Accounts | Identify | IG1 |
| Safeguard 5.2 | Use Unique Passwords | Protect | IG1 |
| Safeguard 5.3 | Disable Dormant Accounts | Protect | IG1 |
| Safeguard 5.4 | Restrict Administrator Privileges to Dedicated Administrator Accounts | Protect | IG1 |
| Safeguard 5.5 | Establish and Maintain an Inventory of Service Accounts | Protect | IG2 |
| Safeguard 5.6 | Centralize Account Management | Govern | IG2 |


