CIS Control 7 Explained: Continuous Vulnerability Management
CIS Control 7 involves continuous vulnerability management. This means developing a process to continuously find and track vulnerabilities in all enterprise assets, in order to remediate and minimize the risk of exploitation. It also includes monitoring public and private sources for new vulnerability information (such as new CVEs).
In this article
The Importance of Control 7
Attackers constantly scan the external infrastructure of organizations to find unpatched weak points to gain entry and therefore defenders must have timely information about new threats and vulnerabilities, as well as know exactly what vulnerabilities are in their infrastructure, if they are actively exploited in the wild and what remediations and workarounds are available.
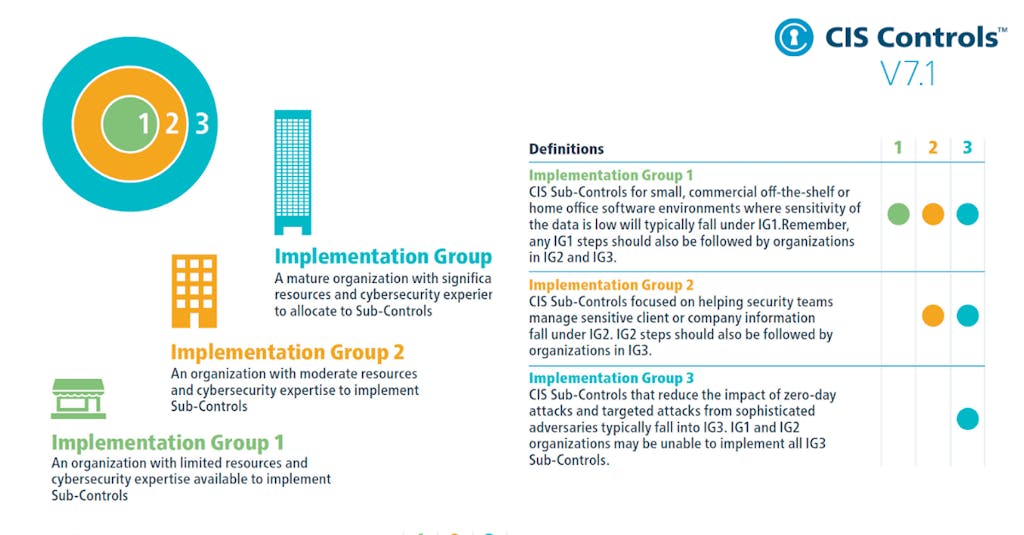
Implementation Groups (IGs)
To implement CIS Controls, follow each listed safeguard, which details the required activities. Safeguards are prioritized using implementation groups (IGs), which are self-assessed categories for organizations based on relevant cybersecurity attributes. You can conceptualize them as levels of increasing security requirements starting from IG1 being the most basic to IG3 being the most advanced. The higher level groups are included in the lower ones.
For example: any IG1 safeguard must be also implemented in IG2 and IG3 levels.
The Safeguards of Control 7
There are seven safeguards in CIS Control 7. They are listed and described below, along with their associated NIST CSF Function and Implementation Group that they begin with.
| Safeguard Number | Safeguard Title | NIST Security Function | StartingImplementation Group |
| Safeguard 7.1 | Establish and Maintain a Vulnerability Management Process | Govern | IG1 |
| Safeguard 7.2 | Establish and Maintain a Remediation Process | Govern | IG1 |
| Safeguard 7.3 | Perform Automated Operating System Patch Management | Protect | IG1 |
| Safeguard 7.4 | Perform Automated Application Patch Management | Protect | IG1 |
| Safeguard 7.5 | Perform Automated Vulnerability Scans of Internal Enterprise Assets | Identify | IG2 |
| Safeguard 7.6 | Perform Automated Vulnerability Scans of Externally-Exposed Enterprise Assets | Identify | IG2 |
| Safeguard 7.7 | Remediate Detected Vulnerabilities | Respond | IG2 |


