CIS Control 8 Explained: Audit Log Management
CIS Control 8 involves audit log management. This means developing a process to collect, alert, review and retain audit logs that can help during security monitoring, threat hunting and incident response.
In this article
The Importance of Control 8
Log collection and analysis are essential for enterprises to quickly identify malicious activities. Audit records often serve as the only evidence of successful attacks. Attackers know that while many organizations keep audit logs for compliance, they may not regularly analyze them. This allows attackers to hide their presence, malicious software and activities on compromised systems. As a result of insufficient or absent log analysis processes, attackers can sometimes maintain control over victim machines for months or even years without the organization’s awareness.
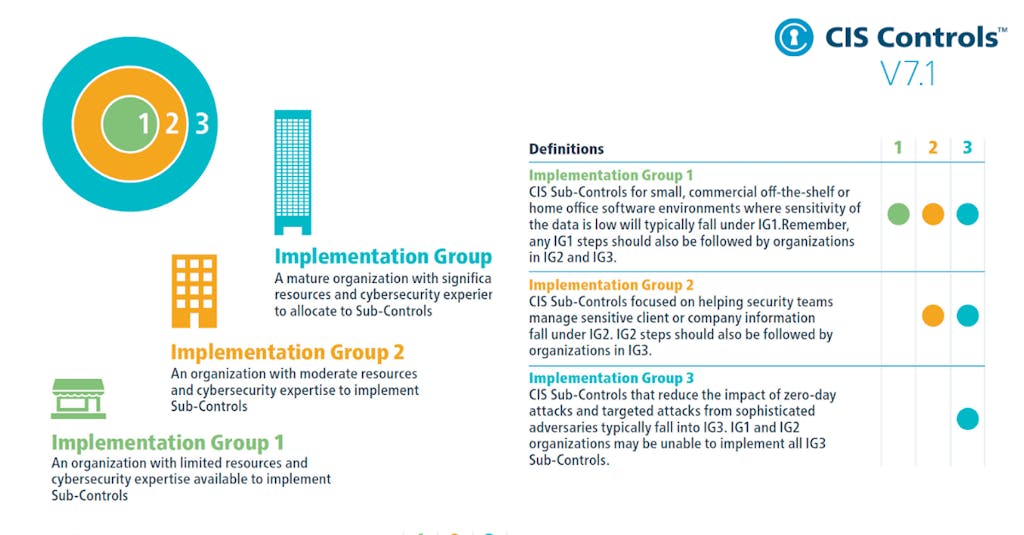
Implementation Groups (IGs)
To implement CIS Controls, follow each listed safeguard, which details the required activities. Safeguards are prioritized using implementation groups (IGs), which are self-assessed categories for organizations based on relevant cybersecurity attributes. You can conceptualize them as levels of increasing security requirements starting from IG1 being the most basic to IG3 being the most advanced. The higher level groups are included in the lower ones.
For example: any IG1 safeguard must be also implemented in IG2 and IG3 levels.
The Safeguards of Control 8
There are twelve safeguards in CIS Control 8. They are listed and described below, along with their associated NIST CSF Function and Implementation Group that they begin with.
| Safeguard Number | Safeguard Title | NIST Security Function | StartingImplementation Group |
| Safeguard 8.1 | Establish and Maintain an Audit Log Management Process | Govern | IG1 |
| Safeguard 8.2 | Collect Audit Logs | Detect | IG1 |
| Safeguard 8.3 | Ensure Adequate Audit Log Storage | Protect | IG1 |
| Safeguard 8.4 | Standardize Time Synchronization | Protect | IG2 |
| Safeguard 8.5 | Collect Detailed Audit Logs | Detect | IG2 |
| Safeguard 8.6 | Collect DNS Query Audit Logs | Detect | IG2 |
| Safeguard 8.7 | Collect URL Request Audit Logs | Detect | IG2 |
| Safeguard 8.8 | Collect Command-Line Audit Logs | Detect | IG2 |
| Safeguard 8.9 | Centralize Audit Logs | Detect | IG2 |
| Safeguard 8.10 | Retain Audit Logs | Protect | IG2 |
| Safeguard 8.11 | Conduct Audit Log Reviews | Detect | IG2 |
| Safeguard 8.12 | Collect Service Provider Logs | Protect | IG3 |


