-
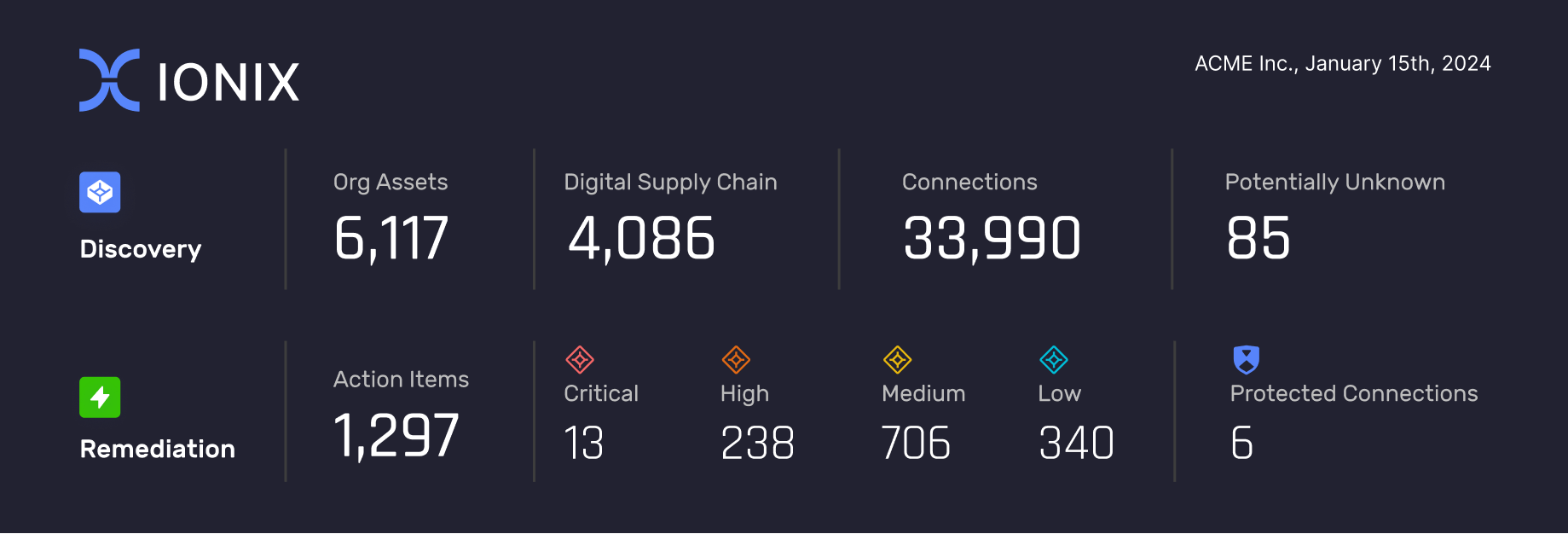
Highlights
DetailsTypeOperated by
- Platform
- Solutions
- Expose and Manage ThreatsContinuously identify, expose and remediate critical threats
- Reduce Attack SurfaceThe roadmap to reducing your attack surface
- Control Subsidiary RiskManage cyber risk across all your subsidiaries
- Cloud Attack SurfaceReduce Cloud Security Noise by Focusing on What Really Matters
- Improve Security PostureReduce risk systematically
- Manage M&A riskEvaluate candidate’s cyber risk
- Threat Center
- Learn
- Company
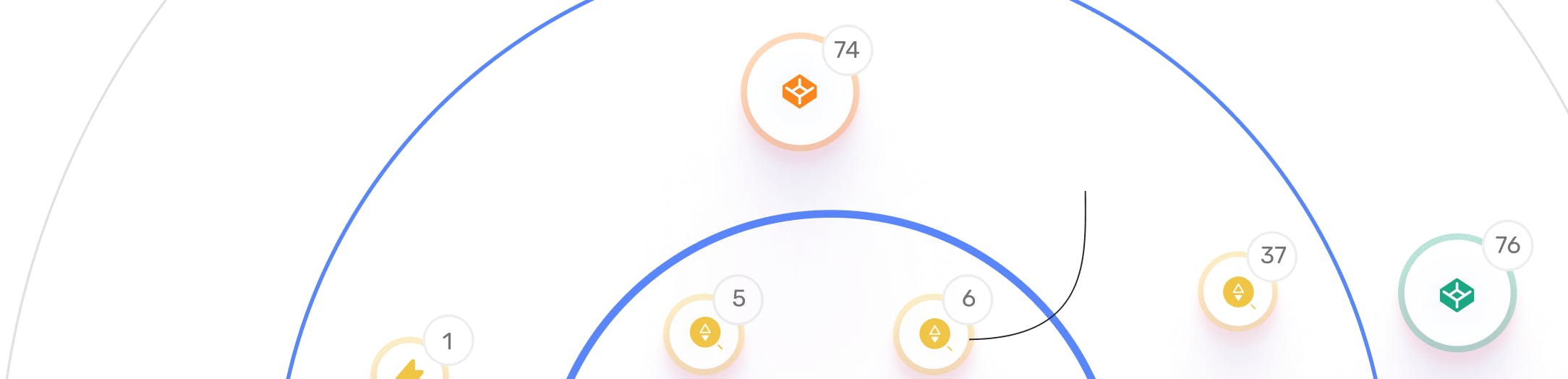
Threat Exposure Radar ExplainedSolutions -
Digital supply-chain risk
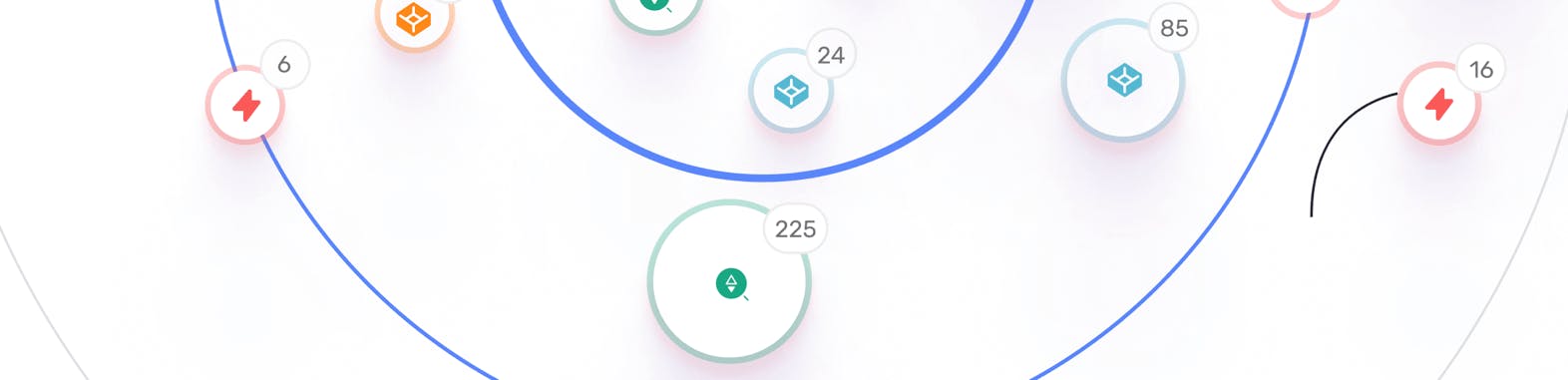
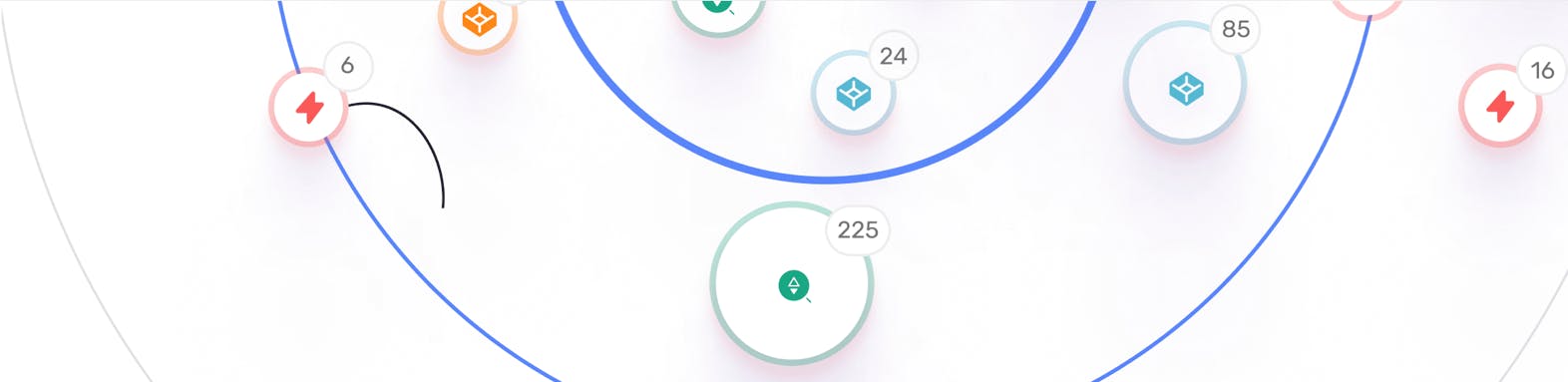
16 risky dependencies on exploitable assets were detected
Action Items
Digital Supply Chain -
Hijackable assets
6 assets could be hijacked via dependency on 3rd party asset
Action Items
External / Digital Supply Chain -
Protected assets
IONIX applied Active Protection on 7 organizational assets to mitigate digital supply-chain vulnerability
Protected Assets
External / Digital Supply Chain -
Potentially unknown assets
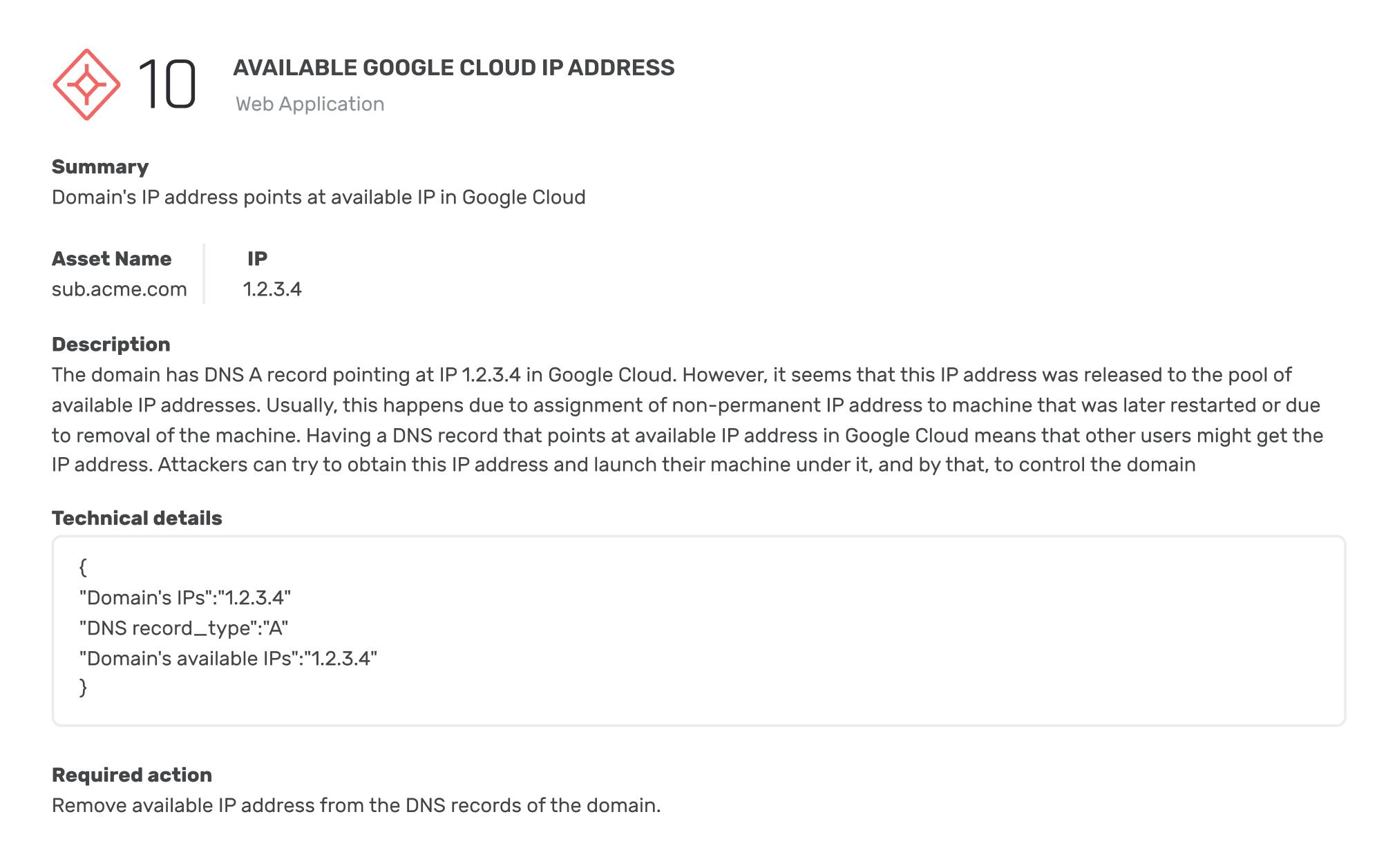
11 misconfigured, potentially unknown, assets were detected in organizational networks
Discovery
Internal Organization -
Potentially unknown assets
74 misconfigured, potentially unknown, assets that are externally hosted
Discovery
External Organization -
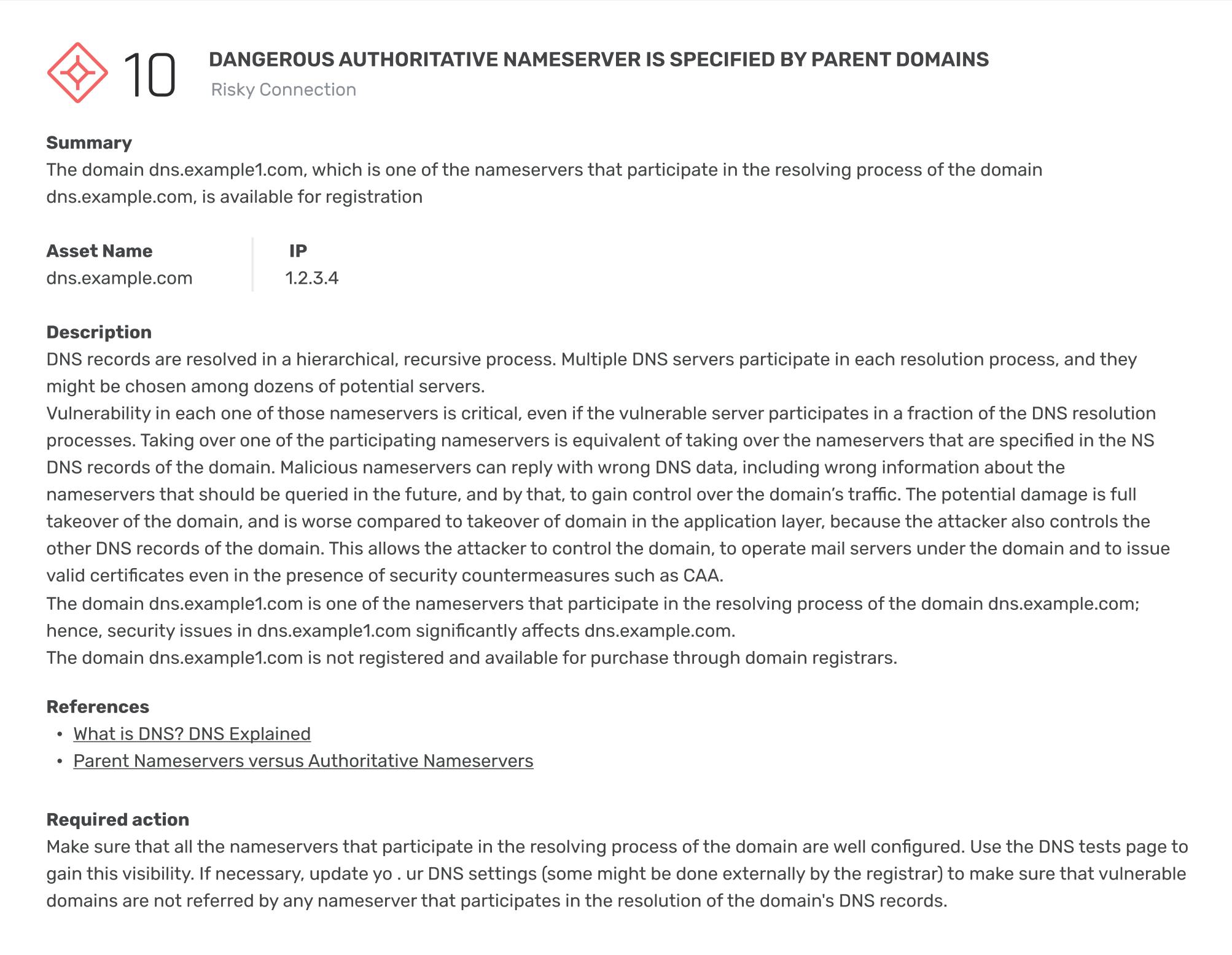
Misconfigured login pages
11 externally hosted login pages are misconfigured and sending data insecurely
Discovery
External Organization -
Potential employee's compromised device
321 potential incidents of employee's compromised device
Cyber Threat Intelligence
Internal / External Org Assets -
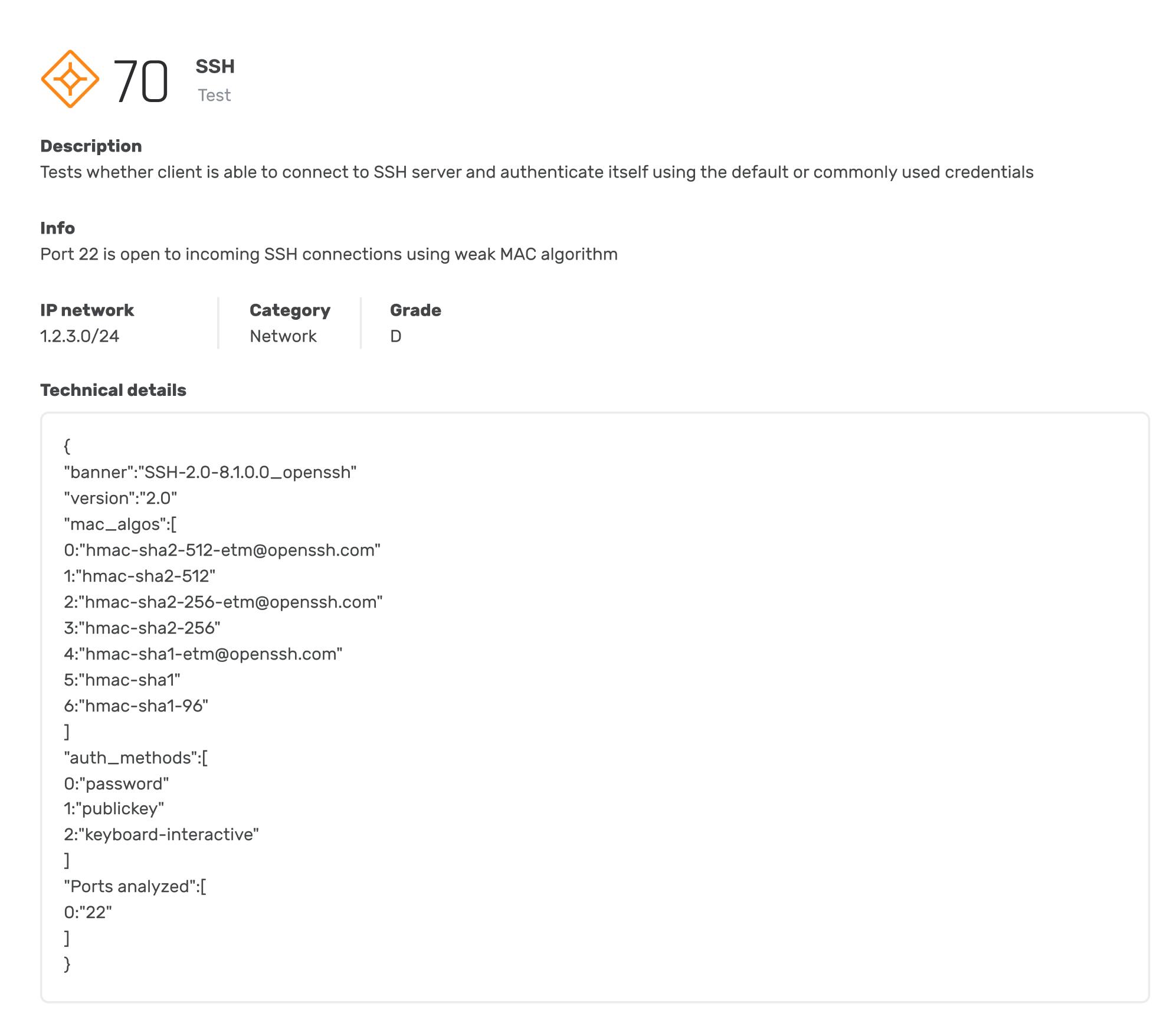
Open SSH Services
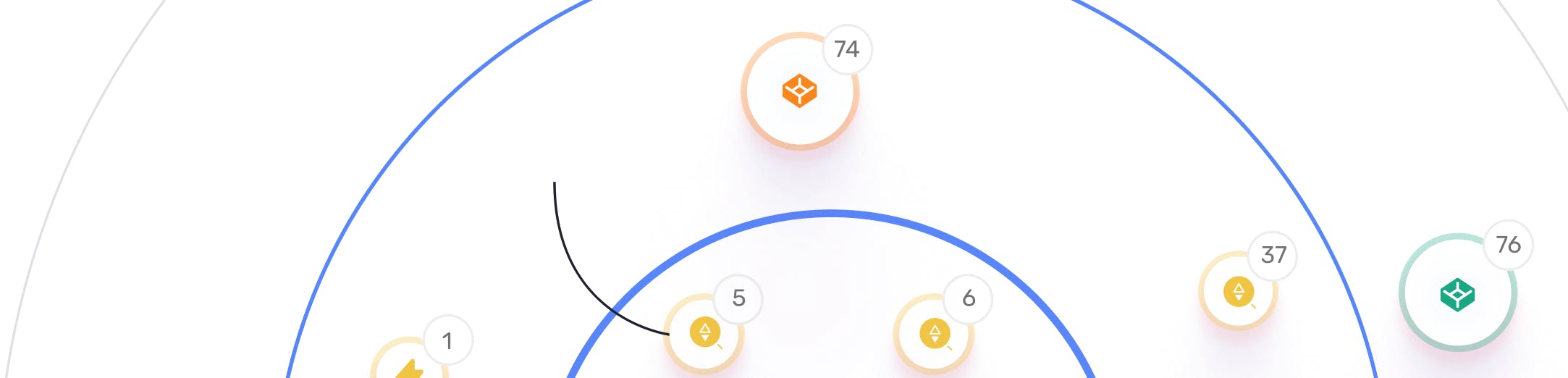
6 open SSH services that are vulnerable to bruteforce attacks were detected in organizational networks
Assessment
Internal Organization -
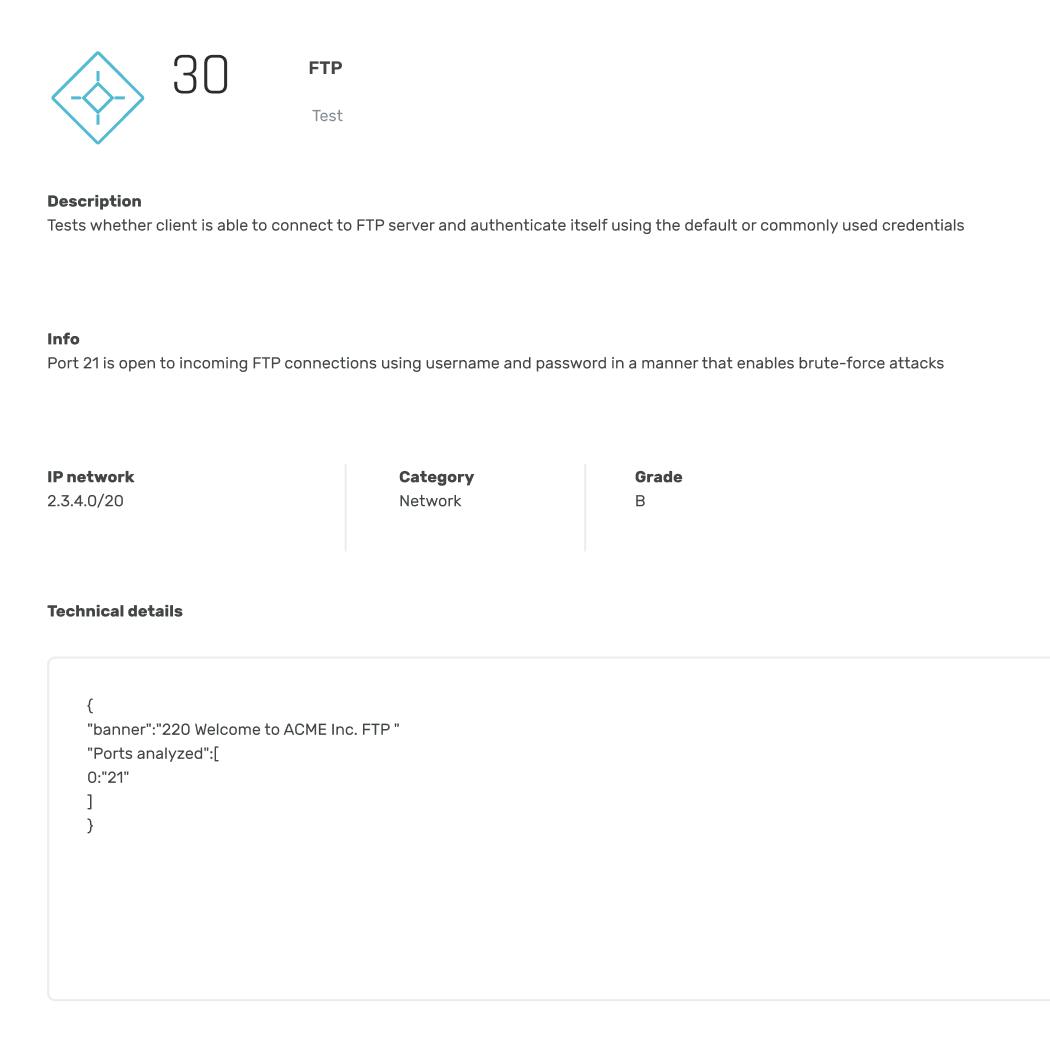
Open FTP Services
5 open FTP services that are vulnerable to bruteforce attack were detected in organizational networks
Assessment
Internal Organization -
Open Network services
37 externally hosted domains expose network a service that is vulnerable to bruteforce attack
Assessment
External Organization -
Exploitable CVEs (medium urgency)
An exploitable CVE with medium urgency in externally hosted asset
Action Items
External Organization -
Dev assets
24 dev assets were detected in organizational networks
Discovery
Internal Organization -
Dev assets
85 externally hosted dev assets were detected
Discovery
External Organization -
Login pages
34 self-hosted login pages
Assessment
Internal Organization -
Login pages
226 externally hosted login pages
Assessment
External Organization -
Digital supply-chain mail servers
76 digital supply-chain mailservers are used by organizational assets
Discovery
Digital Supply Chain -
Digital supply-chain script sources
Organizational assets load code from 225 digital supply-chain assets
Discovery
Digital Supply Chain
IONIX Cloud Exposure ValidatorProductFREE THREAT EXPOSURE REPORT
Get a comprehensive report of your complete attack surface exposure. The content below is excerpted from an actual attack surface exposure report from an IONIX customer.
SCAN REPORT COVERAGE AREAS
Internal Org Assets
Assets hosted in the organizational network (in their on-premise data centers or controlled cloud environments)
External Org Assets
Assets hosted outside of the organizational network (hosting providers, non-controlled cloud environments and others)
Digital Supply Chain
Assets that the organization relies on, but does not own (Mail or DNS servers, Script Inclusion, APIs or others)
Threat Report Highlights
Discover the full extent of your online exposure with our customized Threat Exposure Report.
Top exposure examples
Digital supply-chain risk16 risky dependencies on exploitable assets were detected
Hijackable assets6 assets could be hijacked via a dependency on 3rd party asset
Open FTP Services5 open FTP services that are vulnerable to bruteforce attack were detected in the organizational networks
Open SSH Services6 open SSH services that are vulnerable to bruteforce attack were detected in the organizational networks
Get a free Threat Exposure Report to understand the specific risks and potential exposures in your complete attack surface.
[FORM: #form]
- Solutions