- Platform
- Solutions
- Expose and Manage ThreatsContinuously identify, expose and remediate critical threats
- Reduce Attack SurfaceThe roadmap to reducing your attack surface
- Control Subsidiary RiskManage cyber risk across all your subsidiaries
- Cloud Attack SurfaceReduce Cloud Security Noise by Focusing on What Really Matters
- Improve Security PostureReduce risk systematically
- Manage M&A riskEvaluate candidate’s cyber risk
- Threat Center
- Learn
- Company
Threat Exposure Radar ExplainedSolutions
IONIX Cloud Exposure ValidatorProductIONIX THREAT EXPOSURE MANAGEMENT
Actionable Insights with One Click
What should you fix now? And what can be safely delayed? This balancing act – at the core of Continuous Threat Exposure Management (CTEM) – is what IONIX Threat Exposure Radar solves, helping you to see and fix only what is urgent and important. The Radar maps key insights and exposures across the attack surface layers and details specific remediation instructions.
PROGRAM SCOPE
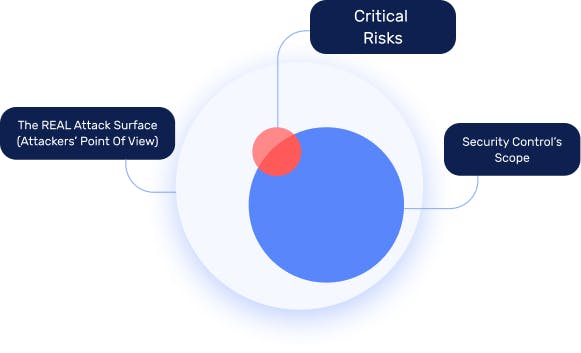
Defend From the Attackers’ Perspective
Critical exposures in the external attack surface are a growing risk in most organizations. Yet siloed security tools offer limited protection across rapidly expanding digital footprints and digital supply chains. This leaves security teams in the dark as they race to find and fix critical exposures before attackers do.
IONIX ASM is a SaaS platform that automates visibility and protection from the attackers’ perspective. The platform provides continuous attack surface discovery, risk assessment, prioritization, and validation to help security teams mobilize and accelerate remediation. In a world where organizations cannot fix everything, IONIX democratizes Threat Exposure making it easy for security and IT teams to identify and act on critical exposures.
CONTINUOUS DISCOVERY
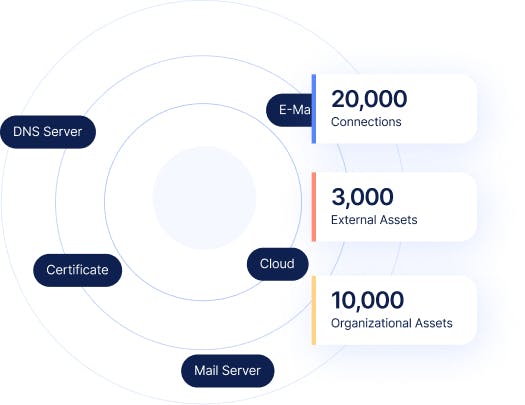
Discover the Extent of Your Exposure
Discover the extent of your internet exposure across hybrid IT on-premises, clouds, managed platforms, and third-party services with IONIX Threat Exposure Management. IONIX provides a holistic view of your organization’s real attack surface and its digital supply chains. With continuous discovery and assessment, IONIX offers Continuous Threat Exposure Management, providing attack surface visibility that automatically adapts to your dynamic IT landscape.
RISK PRIORITIZATION
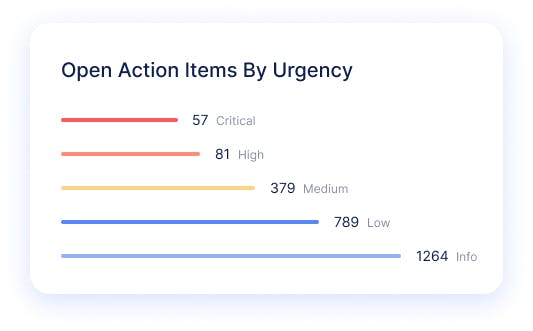
Prioritize with Organizational Context and Threat Intelligence
Stay laser-focused on the most urgent and exploitable risks to your business with IONIX’s prioritization framework. Prioritize exploitable threats requiring immediate remediation and map the blast radius to assess the impact on your business with threat exposure management. Contextualize threat intelligence by correlating compromised device findings with your asset inventory.
SECURITY VALIDATION
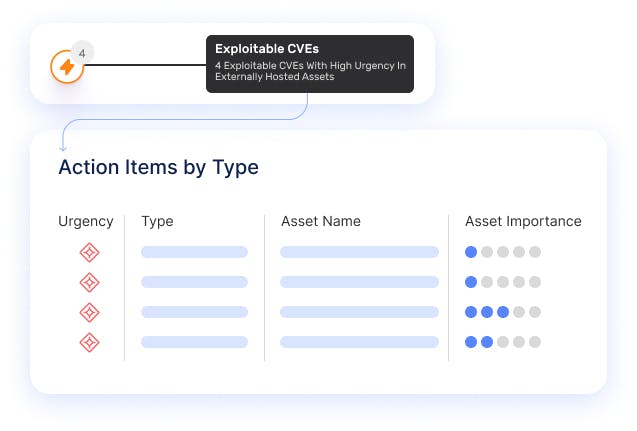
Expose Your Real Threats with Security Validation
Go beyond banner scraping to continuously conduct security testing across your attack surface, including production systems, with IONIX Exposure Validation. Actively validate vulnerabilities and expose critical misconfigurations. Map attack paths from your digital supply chains that put your organizational assets at risk with Continuous Threat Exposure Management.
MOBILIZATION AND REMEDIATION
Reduce Risk with Focused Remediation and Simpler Collaboration
IONIX’s workflows align remediation tasks with the way that security operations actually work – so you spend less time on routing tickets, and more time resolving critical risks. Seamless integration with security information and event management (SIEM) systems, SOAR, security operations center (SOC) software, and ticketing systems helps security teams reduce risks, faster.
WATCH A SHORT IONIX DEMO
See how easy it is to implement a CTEM program with IONIX. Find and fix exploits fast.
- Solutions